Hi!
In this article, I will show you how you can enable Advanced Threat Protection for Azure Cosmos DB. This will help you to detect anomalous activities indicating unusual and potentially harmful attempts to access or exploit databases. Two types of alerts can be detected:
- Access from unusual locations: This alert is triggered when there is a change in the access pattern to an Azure Cosmos account, where someone has connected to the Azure Cosmos DB endpoint from an unusual geographical location. In some cases, the alert detects a legitimate action, meaning a new application or developer’s maintenance operation. In other cases, the alert detects a malicious action from a former employee, external attacker, etc.
- Unusual data extraction: This alert is triggered when a client is extracting an unusual amount of data from an Azure Cosmos DB account. This can be the symptom of some data exfiltration performed to transfer all the data stored in the account to an external data store.
It can currently trigger the following alerts:
| Alert | Description | MITRE tactics | Severity |
|---|---|---|---|
| PREVIEW – Access from an unusual location to a Cosmos DB account | Indicates that there was a change in the access pattern to an Azure Cosmos DB account. Someone has accessed this account from an unfamiliar IP address, compared to recent activity. Either an attacker has accessed the account, or a legitimate user has accessed it from a new and unusual geographical location. An example of the latter is remote maintenance from a new application or developer. | Exploitation | Medium |
| PREVIEW – Unusual amount of data extracted from a Cosmos DB account | Indicates that there was a change in the data extraction pattern from an Azure Cosmos DB account. Someone has extracted an unusual amount of data compared to recent activity. An attacker might have extracted a large amount of data from an Azure Cosmos DB database (for example, data exfiltration or leakage, or an unauthorized transfer of data). Or, a legitimate user or application might have extracted an unusual amount of data from a container (for example, for maintenance backup activity). | Exfiltration | Medium |
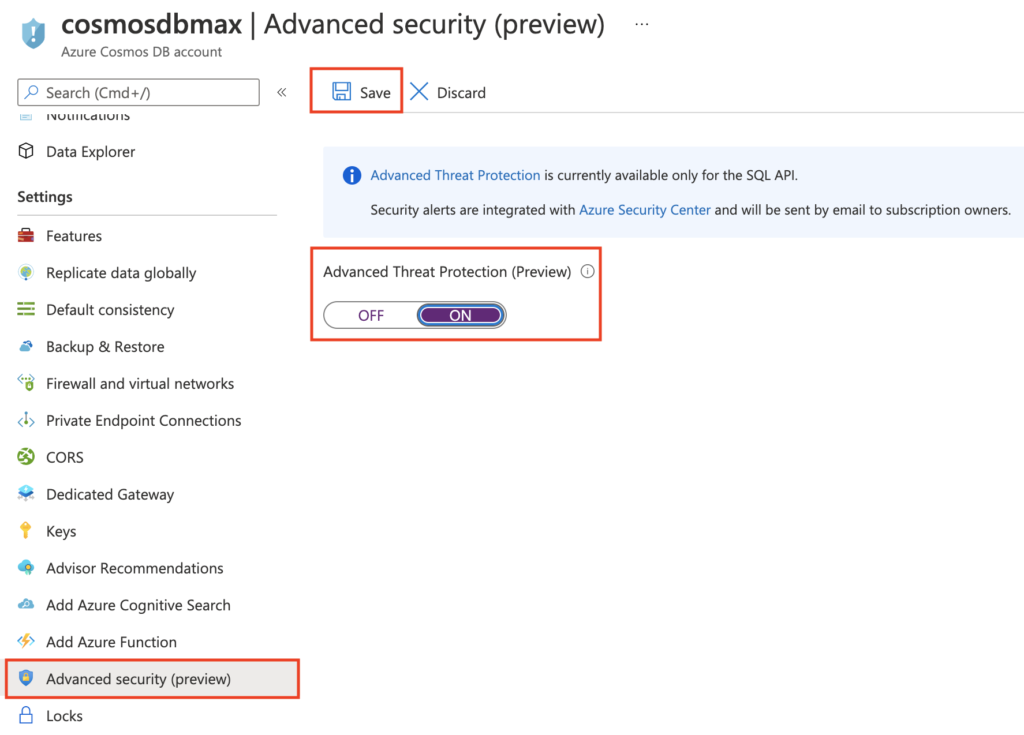
To enable Advanced Threat Protection for Azure Cosmos DB:
Select your Azure Cosmos DB account > Settings > Advanced security (preview) > Advanced Threat Protection (Preview) On > Save.
Maxime.
