Hi!
With the release of Microsoft Defender for Containers, Microsoft merged two existing Defender plans:
- Defender for Kubernetes
- Defender for container registries
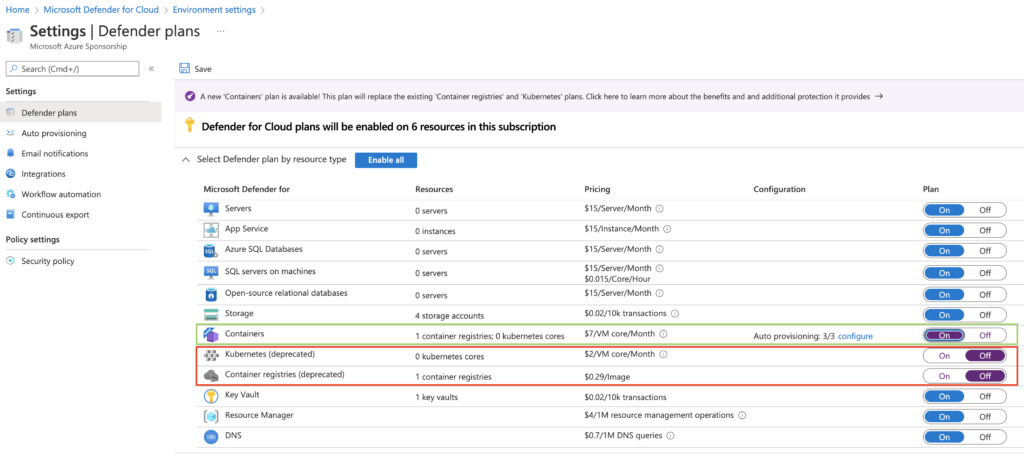
The new plan:
- Combines the features of the two existing plans – threat detection for Kubernetes clusters and vulnerability assessment for images stored in container registries
- Brings new and improved features – including multi-cloud support, host level threat detection with over sixty new Kubernetes-aware analytics, and vulnerability assessment for running images
- Introduces Kubernetes-native at-scale onboarding – by default, when you enable the plan all relevant components are configured to be deployed automatically
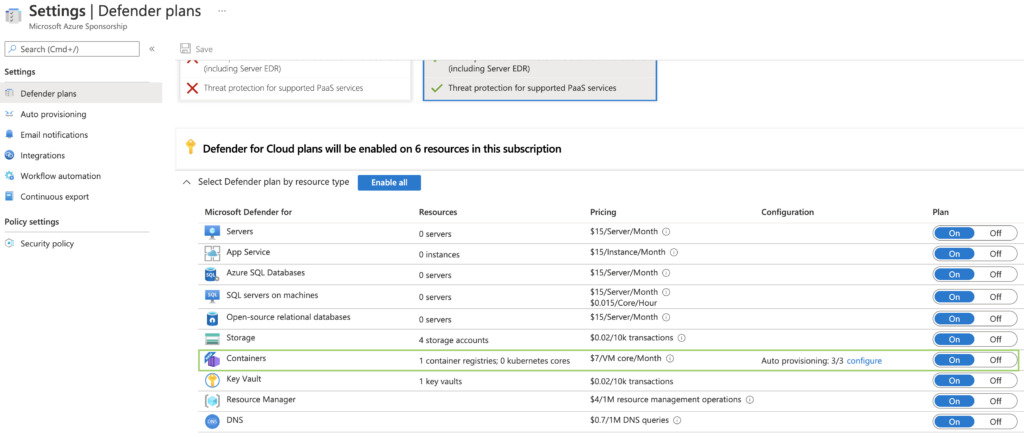
To enable this new plan, please follow the following steps:
- Microsoft Defender for Cloud >
- In the “Management” section >
- Environment settings >
- Select your subscription >
- Click on “On” for Containers >
- Save
Maxime.
