Hi!
In this article, I will show you how you can leverage the MicroBurst tool to anonymously enumerating Azure Services.
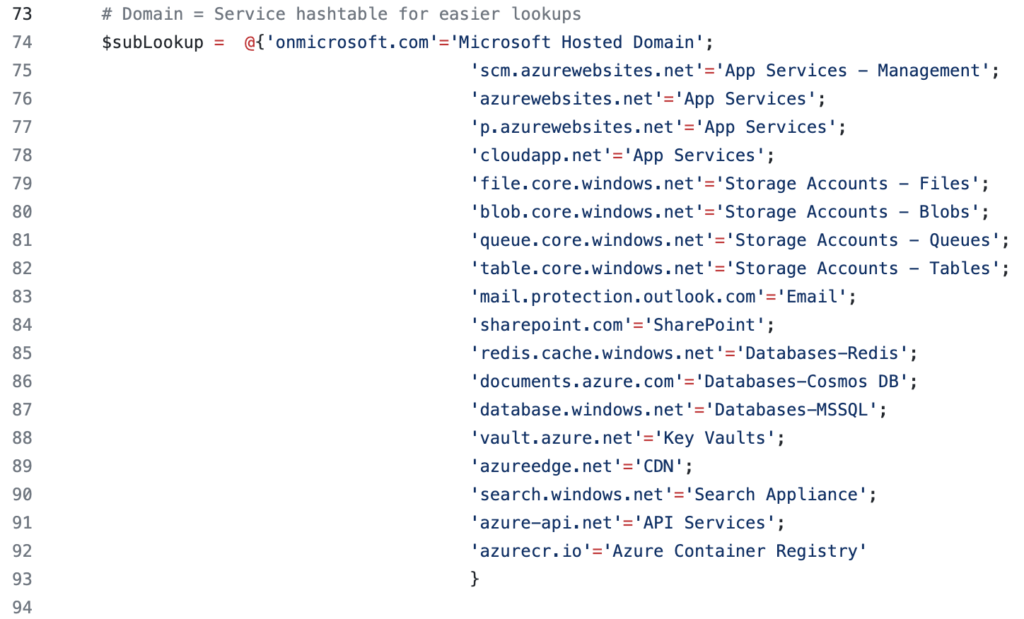
Please find below a list of DNS suffixes associated with the Azure Services:
| DNS Suffix | Associated Azure Service |
| file.core.windows.net | Storage Accounts – Files |
| blob.core.windows.net | Storage Accounts – Blobs |
| queue.core.windows.net | Storage Accounts – Queues |
| table.core.windows.net | Storage Accounts – Tables |
| azurewebsites.net | App Services and Function app |
| scm.azurewebsites.net | App Services – Management |
| database.windows.net | Databases – MSSQL |
| documents.azure.com | Databases – Cosmos DB |
| azurecontainer.io | Container Instances |
| azurecr.io | Container Registry |
| redis.cache.windows.net | Redis |
| azureedge.net | CDN |
| search.windows.net | Search Appliance |
| azure-api.net | API Services |
| cloudapp.azure.com | Customer-assigned public IP DNS |
| vault.azure.net | Key Vault |
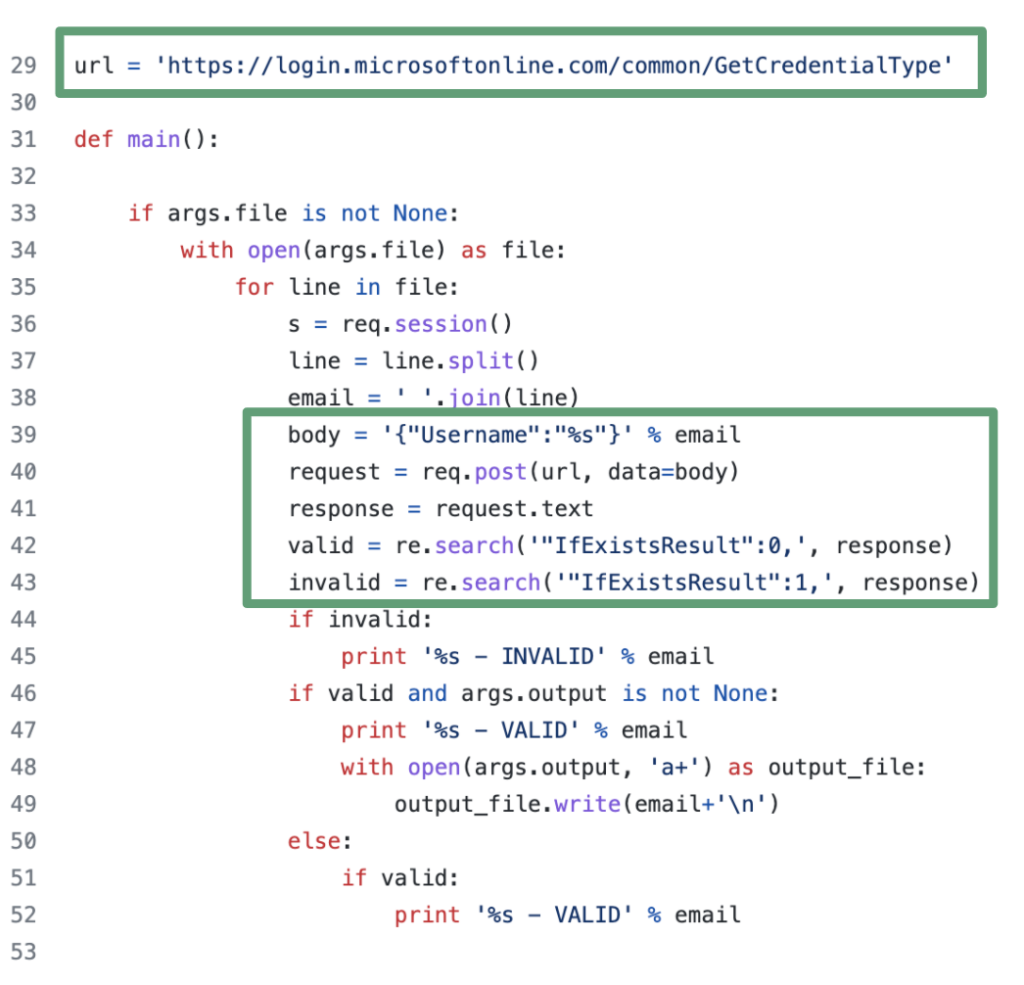
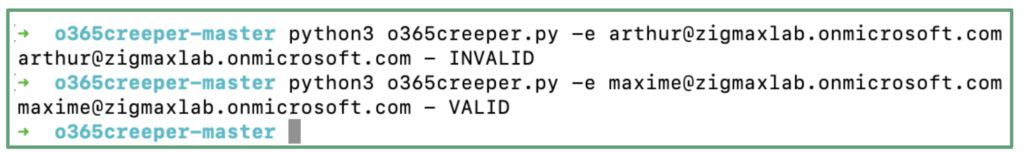
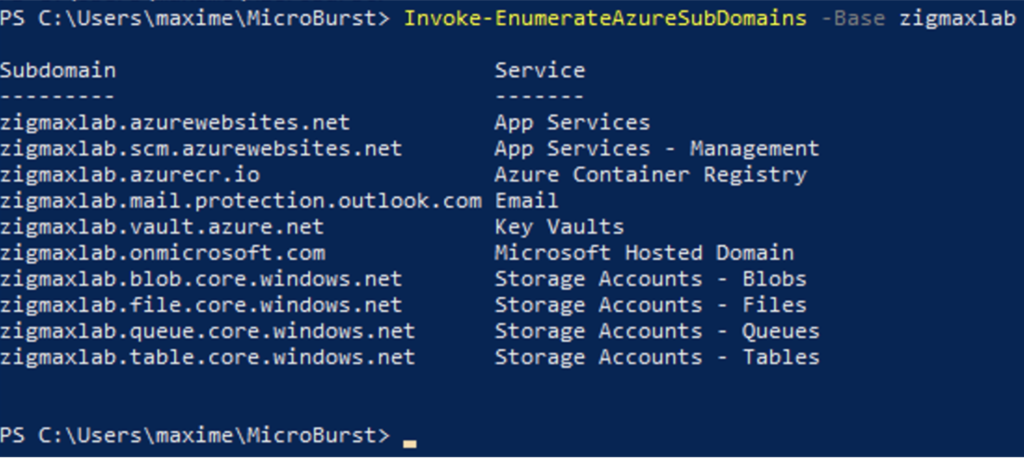
To conduct this enumeration, we will use the MicroBurst tool.
git clone https://github.com/NetSPI/MicroBurst.git
Import-Module .\MicroBurst.psm1
Invoke-EnumerateAzureSubDomains -Base yourkeyword (you can also add a list of permutations with the parameter -Permutations ".\permutations.txt")
Maxime.