Salut!
Après vu ensemble comment déployer un cluster AKS, nous allons voir ensemble dans cet article comment déployer une application à l’intérieur de celui-ci. Nous utiliserons la registry que nous avons pu créer dans un précédent article.
maxime@Azure:~$ az acr list --resource-group k8smaxdemo --query "[].{acrLoginServer:loginServer}" --output table
AcrLoginServer
------------------------
k8smaxdemoacr.azurecr.io
vi aks_to_acr.sh #!/bin/bash # Grant AKS access to ACR AKS_RESOURCE_GROUP=k8smaxdemo AKS_CLUSTER_NAME=myK8sCluster ACR_RESOURCE_GROUP=k8smaxdemo ACR_NAME=k8smaxdemoacr # Get the id of the service principal configured for AKS CLIENT_ID=$(az aks show --resource-group $AKS_RESOURCE_GROUP --name $AKS_CLUSTER_NAME --query "servicePrincipalProfile.clientId" --output tsv) # Get the ACR registry resource id ACR_ID=$(az acr show --name $ACR_NAME --resource-group $ACR_RESOURCE_GROUP --query "id" --output tsv) # Create role assignment az role assignment create --assignee $CLIENT_ID --role Reader --scope $ACR_ID
maxime@Azure:~$ ./aks_to_acr.sh
{
"id": "/subscriptions/7db5e03c-xxxx-xxxx-xxxx-xxxxxxxxxxxx/resourceGroups/k8smaxdemo/providers/Microsoft.ContainerRegistry/registries/k8smaxdemoacr/providers/Microsoft.Authorization/roleAssignments/85f55dfb-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"name": "85f55dfb-xxxx-xxxx-xxxx-xxxxxxxxxxxxx",
"properties": {
"additionalProperties": {
"createdBy": null,
"createdOn": "2018-02-03T19:54:33.0900849Z",
"updatedBy": "56dfc2de-7c4d-4b8a-bf7b-d63cdeae5907",
"updatedOn": "2018-02-03T19:54:33.0900849Z"
},
"principalId": "f6700ac3-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"roleDefinitionId": "/subscriptions/7db5e03c-xxxx-xxxx-xxxx-xxxxxxxxxxxx/providers/Microsoft.Authorization/roleDefinitions/acdd
72a7-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"scope": "/subscriptions/7db5e03c-xxxx-xxxx-xxxx-xxxxxxxxxxxx/resourceGroups/k8smaxdemo/providers/Microsoft.ContainerRegistry/r
egistries/k8smaxdemoacr"
},
"resourceGroup": "k8smaxdemo",
"type": "Microsoft.Authorization/roleAssignments"
}
vi aks_secrets.sh #!/bin/bash # Access with Kubernetes Secrets ACR_NAME=k8smaxdemoacr SERVICE_PRINCIPAL_NAME=acr-service-principal # Populate the ACR login server and resource id. ACR_LOGIN_SERVER=$(az acr show --name $ACR_NAME --query loginServer --output tsv) ACR_REGISTRY_ID=$(az acr show --name $ACR_NAME --query id --output tsv) # Create a contributor role assignment with a scope of the ACR resource. SP_PASSWD=$(az ad sp create-for-rbac --name $SERVICE_PRINCIPAL_NAME --role Reader --scopes $ACR_REGISTRY_ID --query password --output tsv) # Get the service principle client id. CLIENT_ID=$(az ad sp show --id http://$SERVICE_PRINCIPAL_NAME --query appId --output tsv) # Output used when creating Kubernetes secret. echo "Service principal ID: $CLIENT_ID" echo "Service principal password: $SP_PASSWD"
maxime@Azure:~$ ./aks_secrets.sh Retrying role assignment creation: 1/36 Service principal ID: 7fb4393b-xxxx-xxxx-xxxx-xxxxxxxxxxxx Service principal password: 8axxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
maxime@Azure:~$ kubectl create secret docker-registry acr-auth --docker-server k8smaxdemoacr.azurecr.io --docker-username 7fb4393b- xxxx-xxxx-xxxx-xxxxxxxxxxxx --docker-password 8axxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx --docker-email max.coquerel@live.fr secret "acr-auth" created
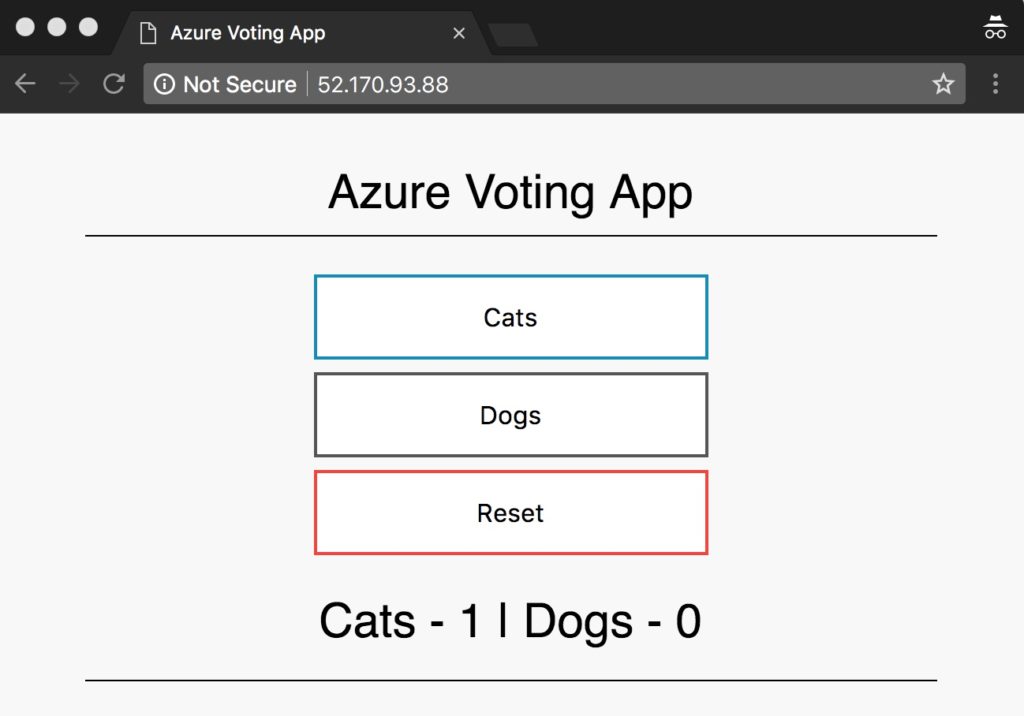
vi azure-vote-all-in-one-redis.yaml apiVersion: apps/v1beta1 kind: Deployment metadata: name: azure-vote-back spec: replicas: 1 template: metadata: labels: app: azure-vote-back spec: containers: - name: azure-vote-back image: redis ports: - containerPort: 6379 name: redis --- apiVersion: v1 kind: Service metadata: name: azure-vote-back spec: ports: - port: 6379 selector: app: azure-vote-back --- apiVersion: apps/v1beta1 kind: Deployment metadata: name: azure-vote-front spec: replicas: 1 template: metadata: labels: app: azure-vote-front spec: containers: - name: azure-vote-front image: k8smaxdemoacr.azurecr.io/microsoft/azure-vote-front:redis-v1 ports: - containerPort: 80 env: - name: REDIS value: "azure-vote-back" imagePullSecrets: - name: acr-auth --- apiVersion: v1 kind: Service metadata: name: azure-vote-front spec: type: LoadBalancer ports: - port: 80 selector: app: azure-vote-front
maxime@Azure:~$ kubectl create -f azure-vote-all-in-one-redis.yaml deployment "azure-vote-back" created service "azure-vote-back" created deployment "azure-vote-front" created service "azure-vote-front" created
maxime@Azure:~$ kubectl get service azure-vote-front --watch NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE azure-vote-front LoadBalancer 10.0.85.75 <pending> 80:30785/TCP 32s azure-vote-front LoadBalancer 10.0.85.75 52.226.17.113 80:30785/TCP 2m
Laisser un commentaire