Hi!
In this article I will show you how you can lock a container image or a repository (so that it can’t be deleted or updated) hosted in Azure Container Registry (ACR).
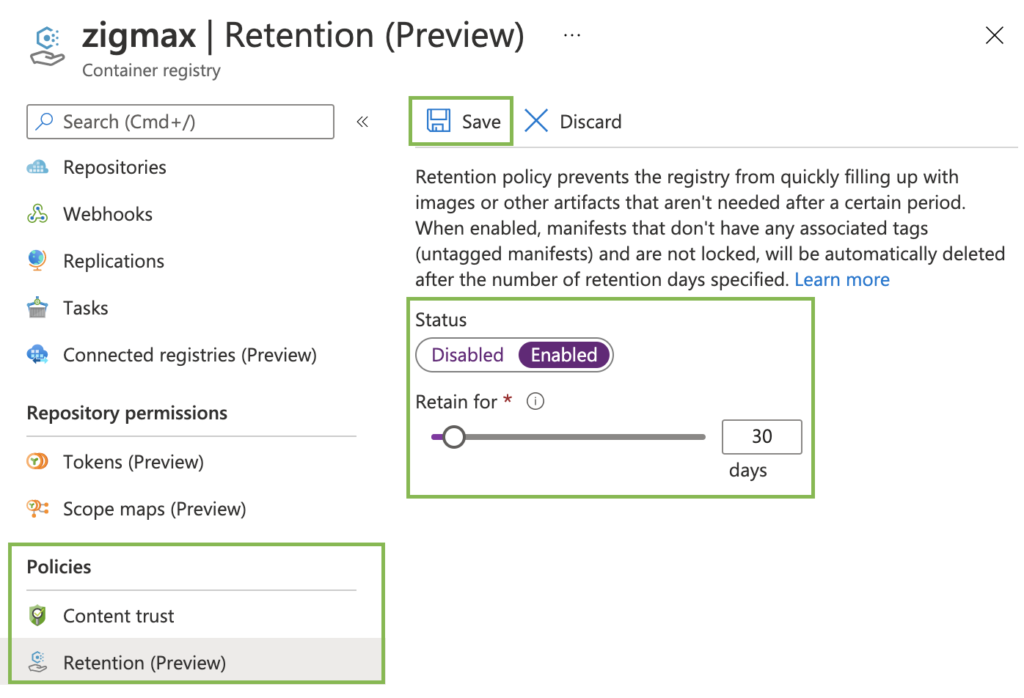
By default, a tagged image in Azure Container Registry is mutable, so with appropriate permissions you can repeatedly update and push an image with the same tag to a registry. Container images can also be deleted as needed. This behavior is useful when you develop images and need to maintain a size for your registry.
However, when you deploy a container image to production, you might need an immutable container image. An immutable image is one that you can’t accidentally delete or overwrite.
Show the current repository attributes
az acr repository show \
--name myregistry --repository myrepo \
--output jsonc
Show the current image attributes
az acr repository show \
--name myregistry --image myimage:tag \
--output jsonc
Lock an image by tag
az acr repository update \
--name myregistry --image myimage:tag \
--write-enabled false
Lock an image by manifest digest
az acr repository update \
--name myregistry --image myimage@sha256:123456abcdefg \
--write-enabled false
Lock a repository
az acr repository update \
--name myregistry --repository myrepo \
--write-enabled false
Protect an image from deletion
az acr repository update \
--name myregistry --repository myrepo \
--delete-enabled false --write-enabled true
Prevent read (pull) operations on an image or repository
az acr repository update \
--name myregistry --image myimage:tag \
--read-enabled false
az acr repository update \
--name myregistry --repository myrepo \
--read-enabled false
Unlock an image or repository
az acr repository update \
--name myregistry --image myimage:tag \
--delete-enabled true --write-enabled true
az acr repository update \
--name myregistry --repository myrepo \
--delete-enabled true --write-enabled true
Maxime.