Hi!
A new Azure Defender plan is available to bring threat protections for the following open-source relational databases:
- Azure Database for PostgreSQL
- Azure Database for MySQL
- Azure Database for MariaDB
The goal of Azure Defender is to detect anomalous activities indicating unusual and potentially harmful attempts to access or exploit databases.
Please find below the list of alerts available:
| Alert (alert type) | Description | MITRE tactics | Severity |
|---|---|---|---|
| Suspected brute force attack using a valid user (SQL.PostgreSQL_BruteForce SQL.MariaDB_BruteForce SQL.MySQL_BruteForce) | A potential brute force attack has been detected on your resource. The attacker is using the valid user (username), which has permissions to login. | PreAttack | High |
| Suspected successful brute force attack (SQL.PostgreSQL_BruteForce SQL.MySQL_BruteForce SQL.MariaDB_BruteForce) | A successful login occurred after an apparent brute force attack on your resource. | PreAttack | High |
| Suspected brute force attack (“SQL.MySQL_BruteForce”) | A potential brute force attack has been detected on your SQL server ‘{name}’. | PreAttack | High |
| Attempted logon by a potentially harmful application (SQL.PostgreSQL_HarmfulApplication SQL.MariaDB_HarmfulApplication SQL.MySQL_HarmfulApplication) | A potentially harmful application attempted to access your resource. | PreAttack | High |
| Login from a principal user not seen in 60 days (SQL.PostgreSQL_PrincipalAnomaly SQL.MariaDB_PrincipalAnomaly SQL.MySQL_PrincipalAnomaly) | A principal user not seen in the last 60 days has logged into your database. If this database is new or this is expected behavior caused by recent changes in the users accessing the database, Security Center will identify significant changes to the access patterns and attempt to prevent future false positives. | Exploitation | Medium |
| Login from a domain not seen in 60 days (SQL.MariaDB_DomainAnomaly SQL.PostgreSQL_DomainAnomaly SQL.MySQL_DomainAnomaly) | A user has logged in to your resource from a domain no other users have connected from in the last 60 days. If this resource is new or this is expected behavior caused by recent changes in the users accessing the resource, Security Center will identify significant changes to the access patterns and attempt to prevent future false positives. | Exploitation | Medium |
| Log on from an unusual Azure Data Center (SQL.PostgreSQL_DataCenterAnomaly SQL.MariaDB_DataCenterAnomaly SQL.MySQL_DataCenterAnomaly) | Someone logged on to your resource from an unusual Azure Data Center. | Probing | Low |
| Logon from an unusual cloud provider (SQL.PostgreSQL_CloudProviderAnomaly SQL.MariaDB_CloudProviderAnomaly SQL.MySQL_CloudProviderAnomaly) | Someone logged on to your resource from a cloud provider not seen in the last 60 days. It’s quick and easy for threat actors to obtain disposable compute power for use in their campaigns. If this is expected behavior caused by the recent adoption of a new cloud provider, Security Center will learn over time and attempt to prevent future false positives. | Exploitation | Medium |
| Log on from an unusual location (SQL.MariaDB_GeoAnomaly SQL.PostgreSQL_GeoAnomaly SQL.MySQL_GeoAnomaly) | Someone logged on to your resource from an unusual Azure Data Center. | Exploitation | Medium |
| Login from a suspicious IP (SQL.PostgreSQL_SuspiciousIpAnomaly SQL.MariaDB_SuspiciousIpAnomaly SQL.MySQL_SuspiciousIpAnomaly) | Your resource has been accessed successfully from an IP address that Microsoft Threat Intelligence has associated with suspicious activity. | PreAttack | Medium |
To enable Azure Defender for open-source relational databases:
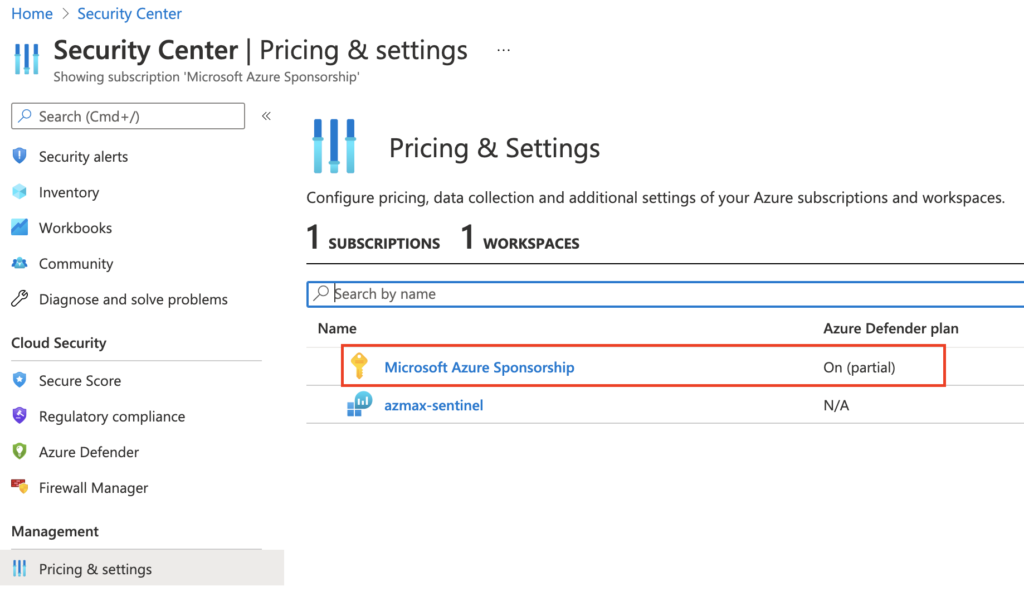
Security Center > Management > Pricing & settings
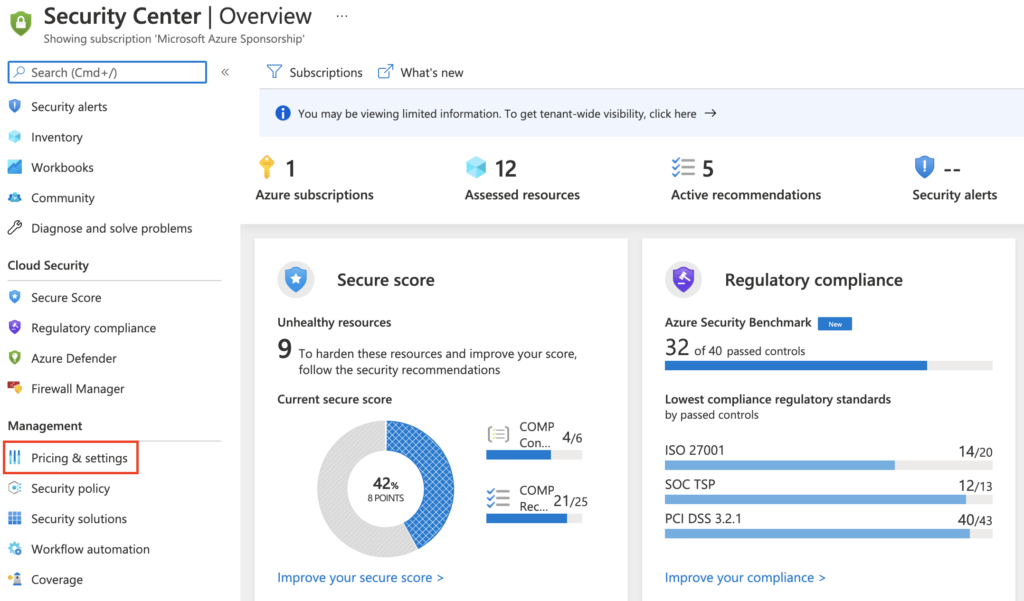
Select your subscription
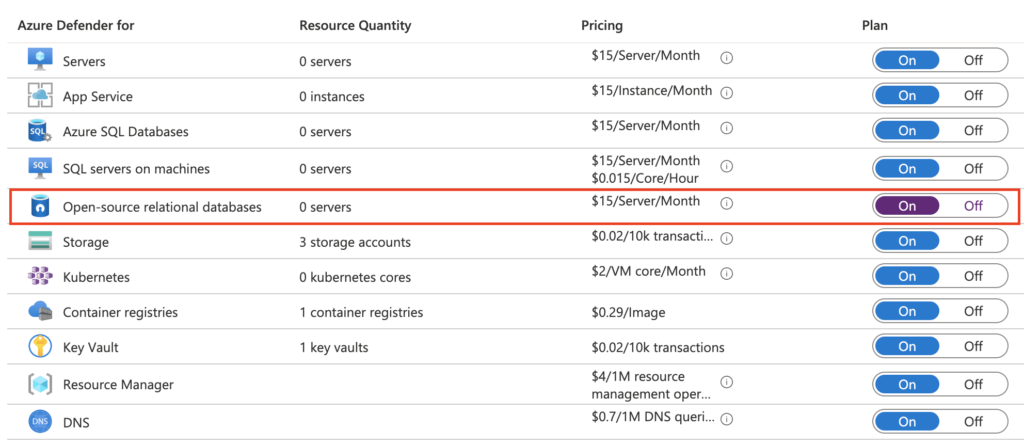
Click-on On for Open-source relational databases and click on Save to save the modification.
Maxime.


