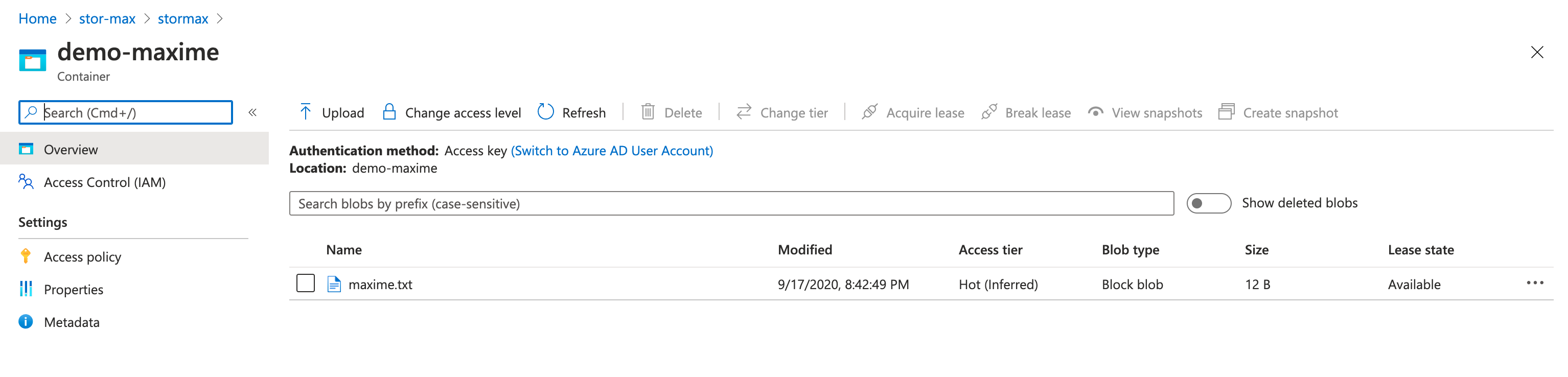
Hi,
In this article, I would like share with you a new feature to start and stop your AKS cluster. This feature is still in public preview. The goal of this feature is to save money!
For example, you can stop your engineering cluster Friday afternoon and restart your AKS cluster Monday morning.
-- Requirements --
Install the aks-preview extension
az extension add --name aks-preview
Update the extension to make sure you have the latest version installed
az extension update --name aks-preview
az feature register --namespace "Microsoft.ContainerService" --name "StartStopPreview"
az feature list -o table --query "[?contains(name, 'Microsoft.ContainerService/StartStopPreview')].{Name:name,State:properties.state}"
az provider register --namespace Microsoft.ContainerService
-- Start a cluster --
az aks start --name myAKSCluster --resource-group myResourceGroup
-- Stop a cluster --
az aks stop --name myAKSCluster --resource-group myResourceGroup
Maxime.