[English version below]
Bonjour,
Dans cet article, je vais vous présenter comment déployer la solution OPA Gatekeeper au sein d’un cluster AKS.
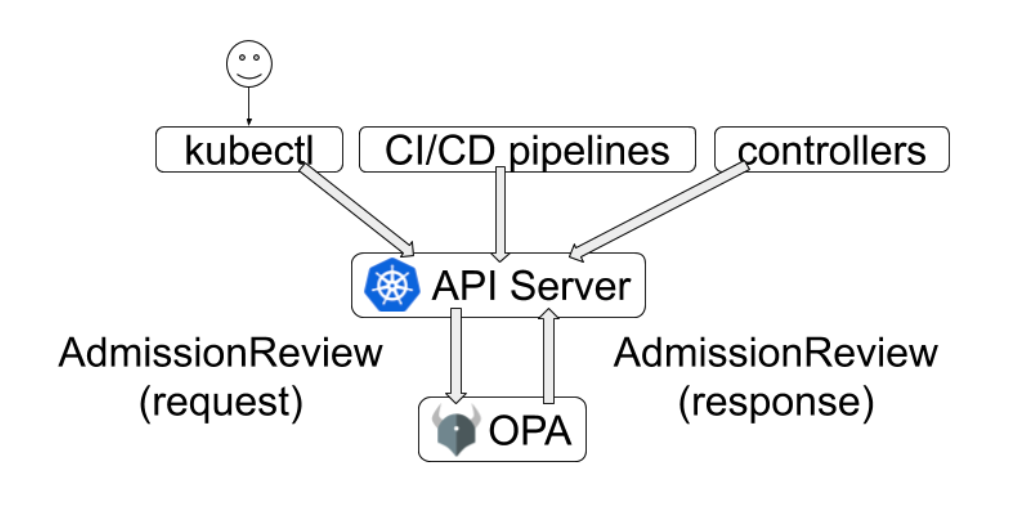
OPA Gatekeeper est un admission controller vous permettant d’auditer et d’appliquer des configurations de sécurité pour vos clusters AKS.
Déployer OPA Gatekeeper (Prebuilt image):
kubectl apply -f https://raw.githubusercontent.com/open-policy-agent/gatekeeper/release-3.1/deploy/gatekeeper.yaml
Dans cet exemple, nous allons créer une policy qui va nécessiter d’avoir le label gatekeeper lors de la création d’un nouveau namespace. Pour cela nous allons créer un template puis une contrainte. Nous verrons dans un second temps comment créer une contrainte en “audit” mode.
Créer un template:
apiVersion: templates.gatekeeper.sh/v1beta1
kind: ConstraintTemplate
metadata:
name: k8srequiredlabels
spec:
crd:
spec:
names:
kind: K8sRequiredLabels
validation:
# Schema for the parameters field
openAPIV3Schema:
properties:
labels:
type: array
items: string
targets:
- target: admission.k8s.gatekeeper.sh
rego: |
package k8srequiredlabels
violation[{"msg": msg, "details": {"missing_labels": missing}}] { provided := {label | input.review.object.metadata.labels[label]} required := {label | label := input.parameters.labels[_]} missing := required - provided count(missing) > 0 msg := sprintf("you must provide labels: %v", [missing]) }
Créer une contrainte:
apiVersion: constraints.gatekeeper.sh/v1beta1
kind: K8sRequiredLabels
metadata:
name: ns-must-have-gk
spec:
match:
kinds:
- apiGroups: [""]
kinds: ["Namespace"]
parameters:
labels: ["gatekeeper"]
Test:
max@Azure:~/clouddrive$ kubectl create namespace maxime
Error from server ([denied by ns-must-have-gk] you must provide labels: {"gatekeeper"}): admission webhook "validation.gatekeeper.sh" denied the request: [denied by ns-must-have-gk] you must provide labels: {"gatekeeper"}
Lister les contraintes:
max_coquerel@Azure:~/clouddrive$ kubectl get constraint
NAME AGE
ns-must-have-gk 80s
Créer une contrainte en mode audit:
apiVersion: constraints.gatekeeper.sh/v1beta1
kind: K8sRequiredLabels
metadata:
name: ns-must-have-gk
spec:
enforcementAction: dryrun
match:
kinds:
- apiGroups: [""]
kinds: ["Namespace"]
parameters:
labels: ["gatekeeper"]
max@Azure:~/clouddrive$ kubectl describe constraint ns-must-have-gk
Name: ns-must-have-gk
Namespace:
Labels:
Annotations:
API Version: constraints.gatekeeper.sh/v1beta1
Kind: K8sRequiredLabels
Status:
Audit Timestamp: 2020-12-30T16:09:13Z
By Pod:
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-audit-576f6d6f8d-kx8p6
Observed Generation: 1
Operations:
audit
status
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-controller-manager-85d8bf48c9-jqhq4
Observed Generation: 1
Operations:
webhook
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-controller-manager-85d8bf48c9-mrj2w
Observed Generation: 1
Operations:
webhook
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-controller-manager-85d8bf48c9-s2d86
Observed Generation: 1
Operations:
webhook
Total Violations: 6
Violations:
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: default
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: gatekeeper-system
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: kube-node-lease
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: kube-public
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: kube-system
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: maxime
Events:
Supprimer une contrainte:
max@Azure:~/clouddrive$ kubectl delete constraint ns-must-have-gk k8srequiredlabels.constraints.gatekeeper.sh "ns-must-have-gk" deleted
Maxime.
Hi,
In this article I will show you, how you can deploy OPA Gatekeeper in your AKS cluster.
OPA Gatekeeper is an admission which can be use to audit the security configuration or your AKS clusters.

Examples of security policies:
- Do not allow privileged containers
- Ensure only allowed container image are allowed
- Prevent host fine system mount
- Enforce labels
- … and more …
Deploy OPA Gatekeeper with the prebuilt image:
kubectl apply -f https://raw.githubusercontent.com/open-policy-agent/gatekeeper/release-3.1/deploy/gatekeeper.yaml
In this article, we will create a new policy. The goal of this policy will to enforce a label at the namespace level. In the first we will create a template and a constraint. In the second part of this article we will see how we can create a constraint in audit mode.
Create a template:
apiVersion: templates.gatekeeper.sh/v1beta1
kind: ConstraintTemplate
metadata:
name: k8srequiredlabels
spec:
crd:
spec:
names:
kind: K8sRequiredLabels
validation:
# Schema for the parameters field
openAPIV3Schema:
properties:
labels:
type: array
items: string
targets:
- target: admission.k8s.gatekeeper.sh
rego: |
package k8srequiredlabels
violation[{"msg": msg, "details": {"missing_labels": missing}}] { provided := {label | input.review.object.metadata.labels[label]} required := {label | label := input.parameters.labels[_]} missing := required - provided count(missing) > 0 msg := sprintf("you must provide labels: %v", [missing]) }
Créer une contrainte:
apiVersion: constraints.gatekeeper.sh/v1beta1
kind: K8sRequiredLabels
metadata:
name: ns-must-have-gk
spec:
match:
kinds:
- apiGroups: [""]
kinds: ["Namespace"]
parameters:
labels: ["gatekeeper"]
Test:
max@Azure:~/clouddrive$ kubectl create namespace maxime
Error from server ([denied by ns-must-have-gk] you must provide labels: {"gatekeeper"}): admission webhook "validation.gatekeeper.sh" denied the request: [denied by ns-must-have-gk] you must provide labels: {"gatekeeper"}
Constraints List:
max_coquerel@Azure:~/clouddrive$ kubectl get constraint
NAME AGE
ns-must-have-gk 80s
Create a constraint in audit mode:
apiVersion: constraints.gatekeeper.sh/v1beta1
kind: K8sRequiredLabels
metadata:
name: ns-must-have-gk
spec:
enforcementAction: dryrun
match:
kinds:
- apiGroups: [""]
kinds: ["Namespace"]
parameters:
labels: ["gatekeeper"]
max@Azure:~/clouddrive$ kubectl describe constraint ns-must-have-gk
Name: ns-must-have-gk
Namespace:
Labels:
Annotations:
API Version: constraints.gatekeeper.sh/v1beta1
Kind: K8sRequiredLabels
Status:
Audit Timestamp: 2020-12-30T16:09:13Z
By Pod:
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-audit-576f6d6f8d-kx8p6
Observed Generation: 1
Operations:
audit
status
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-controller-manager-85d8bf48c9-jqhq4
Observed Generation: 1
Operations:
webhook
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-controller-manager-85d8bf48c9-mrj2w
Observed Generation: 1
Operations:
webhook
Constraint UID: b245e684-174d-4b28-8be0-064722f2b4a3
Enforced: true
Id: gatekeeper-controller-manager-85d8bf48c9-s2d86
Observed Generation: 1
Operations:
webhook
Total Violations: 6
Violations:
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: default
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: gatekeeper-system
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: kube-node-lease
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: kube-public
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: kube-system
Enforcement Action: dryrun
Kind: Namespace
Message: you must provide labels: {"gatekeeper"}
Name: maxime
Events:
Remove a constraint:
max@Azure:~/clouddrive$ kubectl delete constraint ns-must-have-gk
k8srequiredlabels.constraints.gatekeeper.sh "ns-must-have-gk" deleted
Maxime.