Hi!
Microsoft added a new capability to easily extract all the details of a specific alert with one button from the security alert’s details pane.
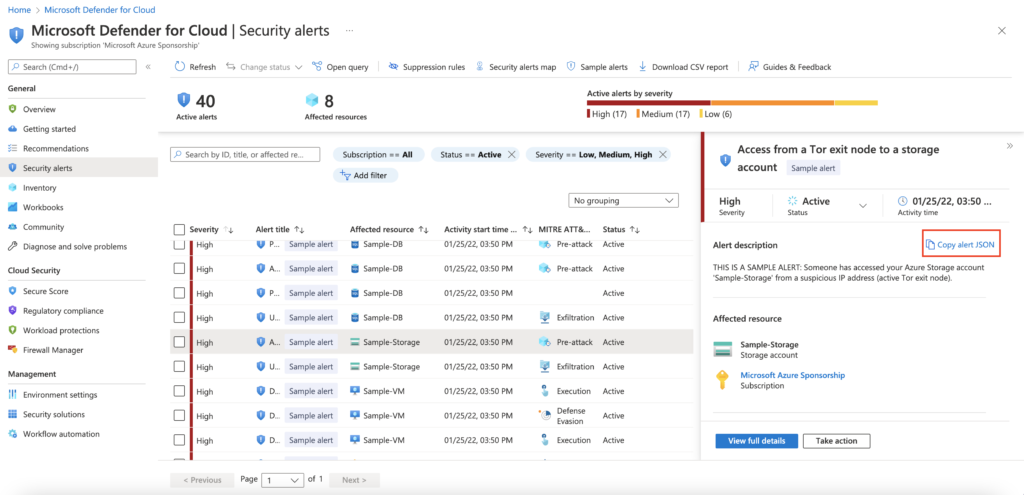
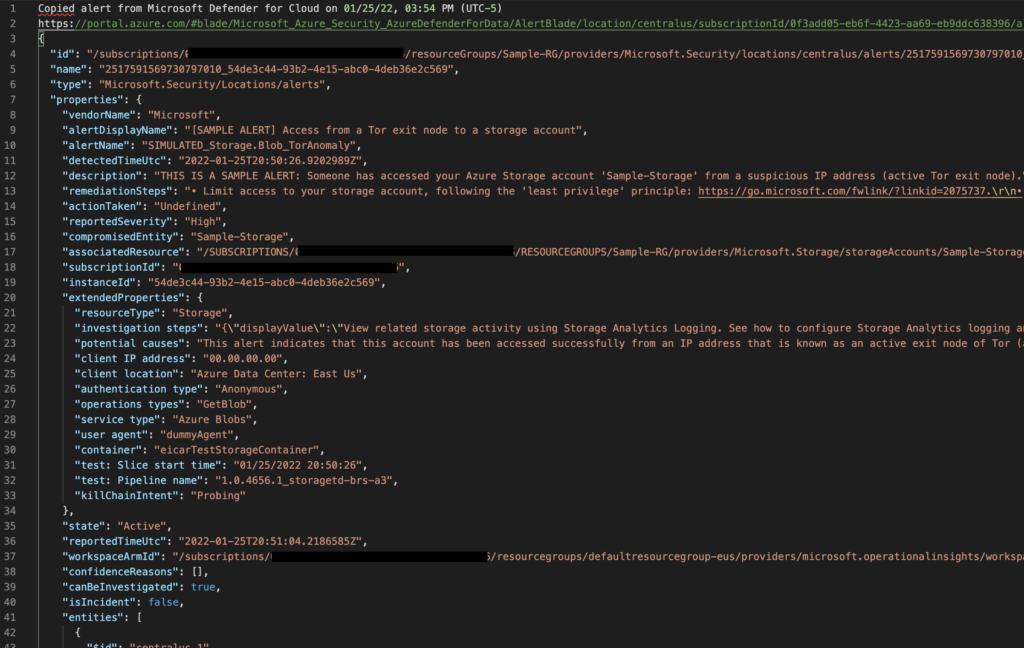
Maxime.
Hi!
In this article, I will share with you a new preview feature of Azure Key Vault. The goal of this feature is to automate the key rotation.
Automated key rotation in Key Vault allows users to configure Key Vault to automatically generate a new key version at a specified frequency. You can use rotation policy to configure rotation for each individual key. Microsoft recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices.
Key Vault key rotation feature requires key management permissions. You can assign a “Key Vault Administrator” role to manage rotation policy and on-demand rotation. If you use an access policies permission model, it is required to set ‘Rotate’, ‘Set Rotation Policy’, and ‘Get Rotation Policy’ key permissions to manage rotation policy on keys.
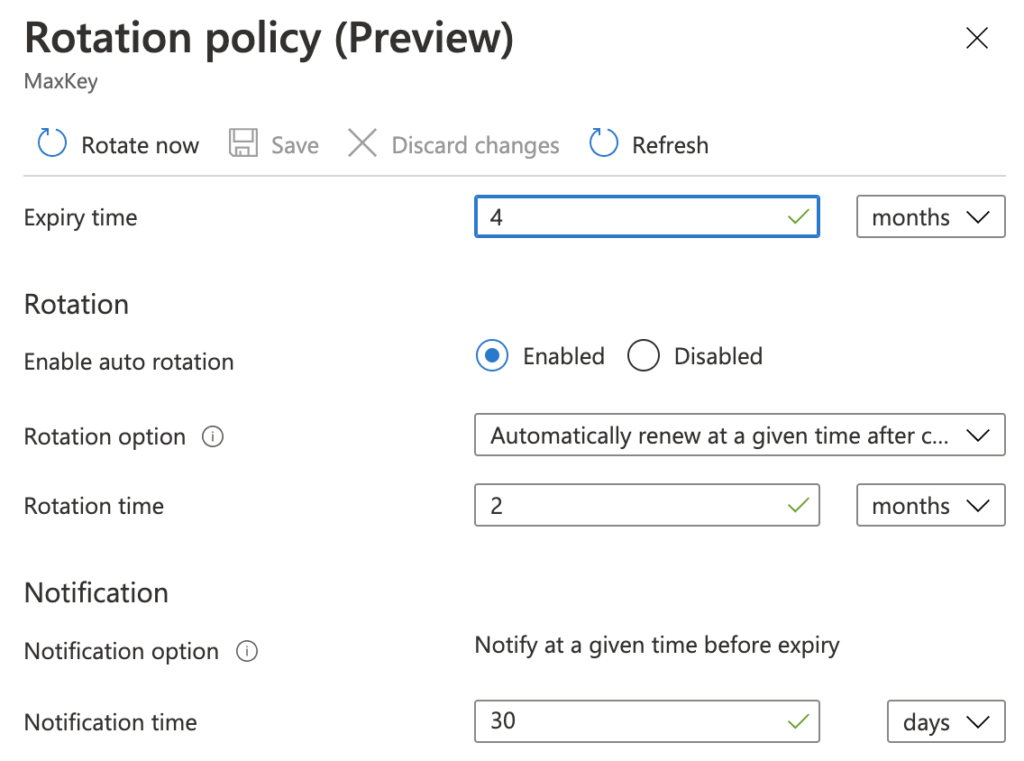
The key rotation policy allows users to configure rotation interval, expiration interval for rotated keys, and near expiry notification period for monitoring expiration using event grid notifications.
Key rotation policy settings:
Configure the key rotation policy:
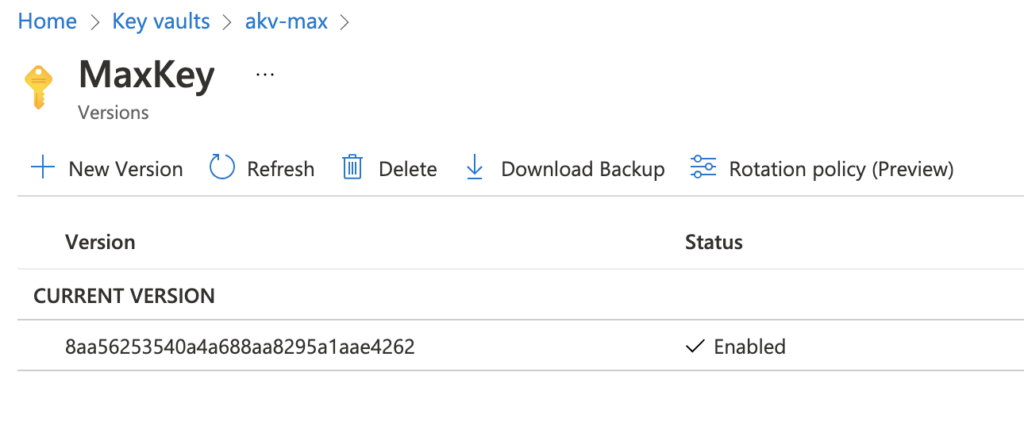
In the following screenshot, we can see an access permission error: the “Get Rotation Policy” is not enabled in this key vault’s access policy.
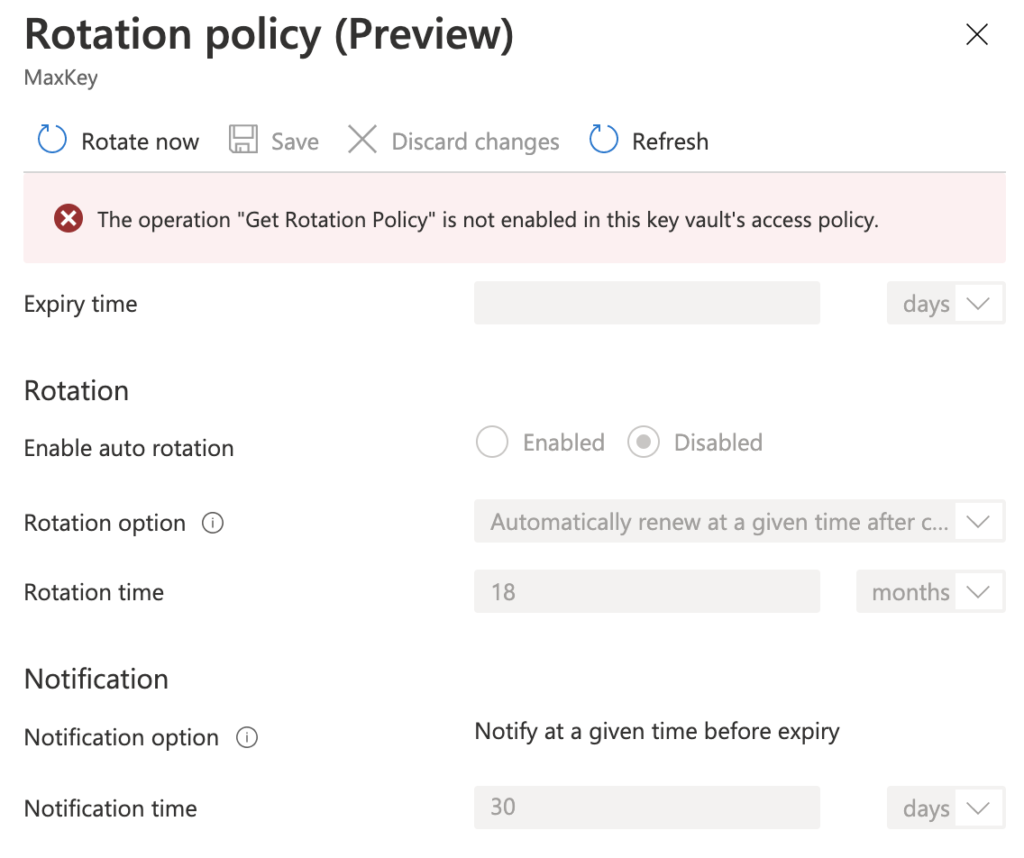
In this step, we will give the rotation policy permissions in the access policy defined for the user max.coq….
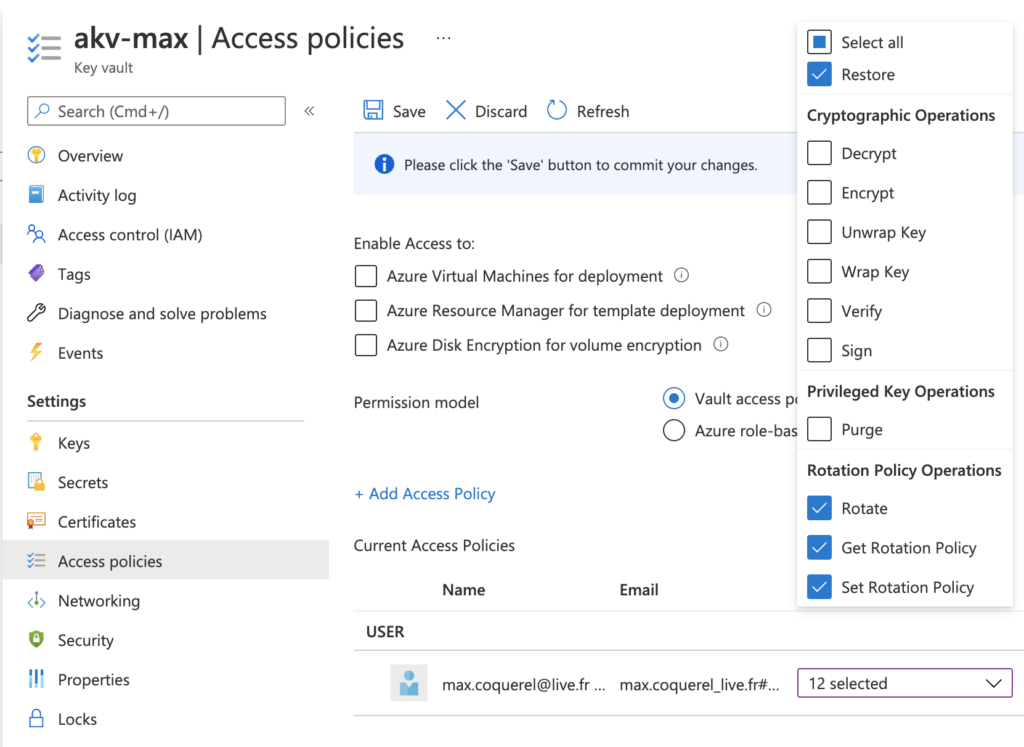
When it’s done, we can define the rotation policy for the key.
Key rotation on-demand:
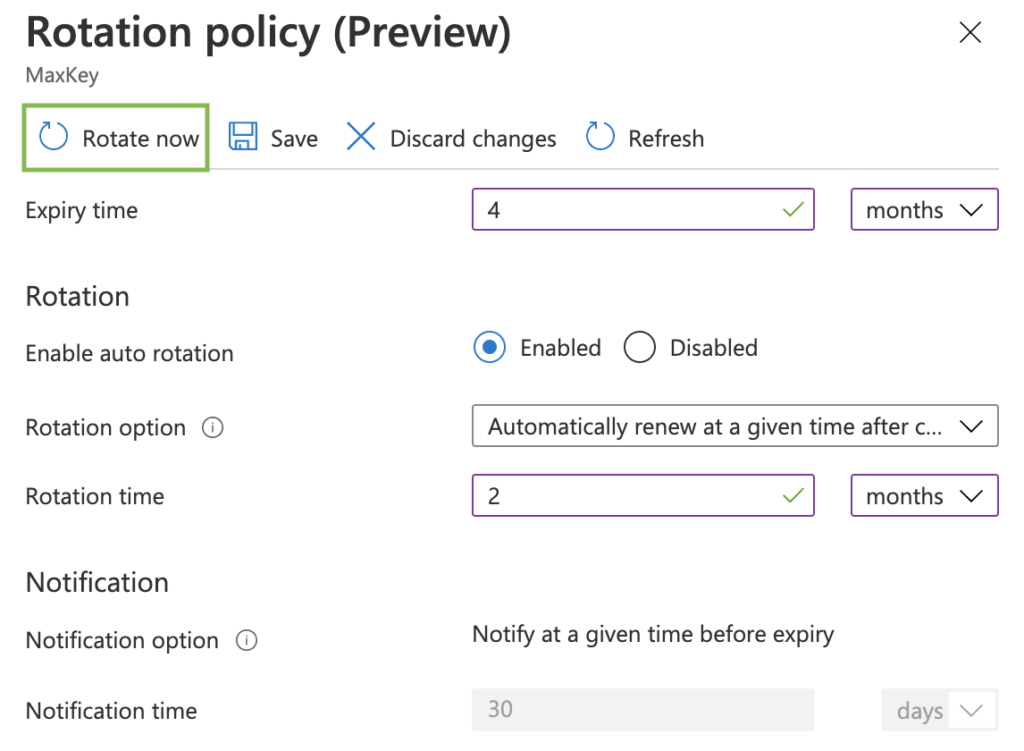
In this step, we will see how we can rotate on-demand a key. In the rotation policy pane, please click on “Rotate Now”.
Click on “Ok” to confirm the key roration.
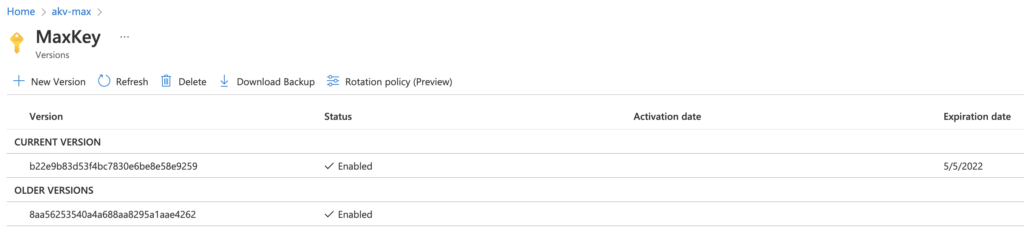
In the screenshot below we can see the new key version.
Maxime.
Hi!
The preview alert that detected this was called “Anonymous scan of public storage containers”. To provide greater clarity about the suspicious events discovered, we’ve divided this into two new alerts. These alerts are relevant to Azure Blob Storage only.
Microsoft has improved the detection logic, updated the alert metadata, and changed the alert name and alert type.
| Alert (alert type) | Description | MITRE tactic | Severity |
|---|---|---|---|
| Publicly accessible storage containers successfully discovered (Storage.Blob_OpenContainersScanning.SuccessfulDiscovery) | A successful discovery of publicly open storage container(s) in your storage account was performed in the last hour by a scanning script or tool. This usually indicates a reconnaissance attack, where the threat actor tries to list blobs by guessing container names, in the hope of finding misconfigured open storage containers with sensitive data in them. The threat actor may use their own script or use known scanning tools like Microburst to scan for publicly open containers. ✔ Azure Blob Storage ✖ Azure Files ✖ Azure Data Lake Storage Gen2 | Collection | Medium |
| Publicly accessible storage containers unsuccessfully scanned (Storage.Blob_OpenContainersScanning.FailedAttempt) | A series of failed attempts to scan for publicly open storage containers were performed in the last hour. This usually indicates a reconnaissance attack, where the threat actor tries to list blobs by guessing container names, in the hope of finding misconfigured open storage containers with sensitive data in them. The threat actor may use their own script or use known scanning tools like Microburst to scan for publicly open containers. ✔ Azure Blob Storage ✖ Azure Files ✖ Azure Data Lake Storage Gen2 | Collection | Low |
Maxime.