Hi,
To expand the threat protections provided by Microsoft Defender for Storage, Microsoft added a new preview alert.
| Alert (alert type) | Description | MITRE tactic | Severity |
|---|---|---|---|
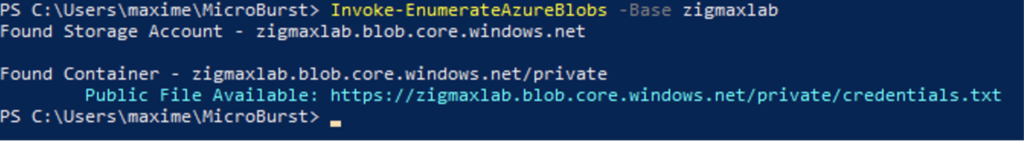
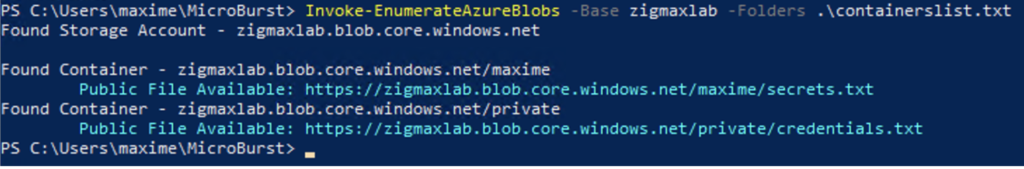
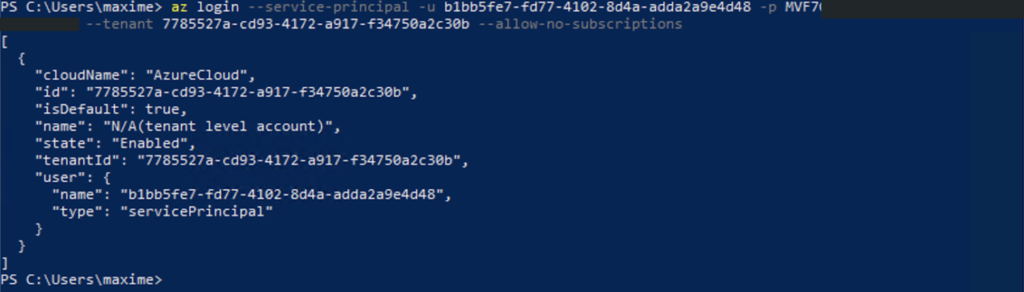
| PREVIEW – Access from a suspicious application (Storage.Blob_SuspiciousApp) | Indicates that a suspicious application has successfully accessed a container of a storage account with authentication. This might indicate that an attacker has obtained the credentials necessary to access the account, and is exploiting it. This could also be an indication of a penetration test carried out in your organization. Applies to: Azure Blob Storage, Azure Data Lake Storage Gen2 | Initial Access | Medium |
Maxime.