Salut!
Aujourd’hui nous allons voir ensemble comment déployer un container SQL Server dans AKS.
vi sqlserver.yaml
apiVersion: apps/v1beta1
kind: Deployment
metadata:
name: sqlserver
labels:
app: sqlserver
spec:
replicas: 1
template:
metadata:
labels:
name: sqlserver
spec:
containers:
- name: sqlserver1
image: microsoft/mssql-server-linux:latest
ports:
- containerPort: 1433
env:
- name: SA_PASSWORD
value: "MonSuperPassword"
- name: ACCEPT_EULA
value: "Y"
---
apiVersion: v1
kind: Service
metadata:
name: sqlserver-service
spec:
ports:
- name: sqlserver
port: 1433
targetPort: 1433
selector:
name: sqlserver
type: LoadBalancer
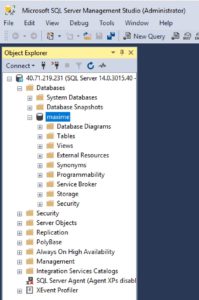
maxime@Azure:~$ kubectl create -f sqlserver.yaml deployment "sqlserver" created service "sqlserver-service" created
maxime@Azure:~$ kubectl get svc --watch sqlserver-service NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE sqlserver-service LoadBalancer 10.0.23.179 40.71.219.231 1433:32462/TCP 1m