Hi!
In this article, I will show you how you can audit your DockerFile with ConfTest.
This tool will help you to write tests against structured configuration data. Using Conftest you can write tests for your Kubernetes configuration, Terraform code, Serverless configs or any other config files.
For this blog post, we will create a ConfTest policies in rego to audit a DockerFile. In this DockerFile, I have included few bad practices and security weakness:
- Hardcoded tokens
- Looking for ADD command instead using COPY command
- Usage of sudo
FROM ubuntu:latest LABEL MAINTAINER "Maxime" ENV SECRET AAAAAAAAAAAAAAAAAAA ENV GITLAB_API_ID aaaaaaaaaaaaaaaaaaaaaaaaaaaaa WORKDIR /app ADD app /app COPY README.md /app/README.md ADD code /tmp/code RUN sudo apt-get udpate RUN apt-get update && apt-get install -y htop CMD ["/bin/bash", "/app/entrypoint.sh"]
Now, we will create a security policy to detect the previous security weakness:
package main
suspicious_env_keys = [
"passwd",
"password",
"secret",
"key",
"access",
"api_key",
"apikey",
"token",
]
# Looking for suspicious environemnt variables
deny[msg] {
input[i].Cmd == "env"
val := input[i].Value
contains(lower(val[_]), suspicious_env_keys[_])
msg = sprintf("Suspicious ENV key found: %s", [val])
}
# Looking for ADD command instead using COPY command
deny[msg] {
input[i].Cmd == "add"
val := concat(" ", input[i].Value)
msg = sprintf("Use COPY instead of ADD: %s", [val])
}
# sudo usage
deny[msg] {
input[i].Cmd == "run"
val := concat(" ", input[i].Value)
contains(lower(val), "sudo")
msg = sprintf("Avoid using 'sudo' command: %s", [val])
}
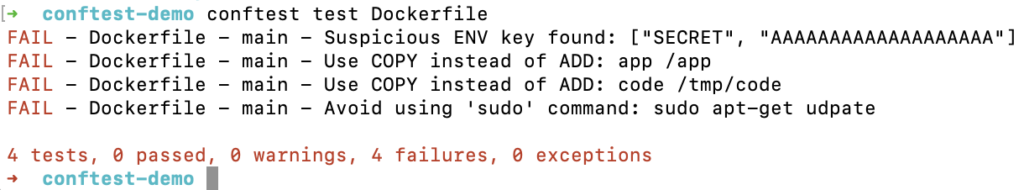
Install ConfTest: https://www.conftest.dev/install/ and run the analyze with the following command:
conftest test Dockerfile
Maxime.


