Hi!
In this article, I would like share with you, how you can deploy an AKS cluster with Confidential nodes.
Let me start with a quick reminder about the confidential computing in Azure. Azure confidential computing allows you to protect your sensitive data while it’s in use. The underlying infrastructures protect this data from other applications, administrators, and cloud providers with a hardware backed trusted execution container environments.
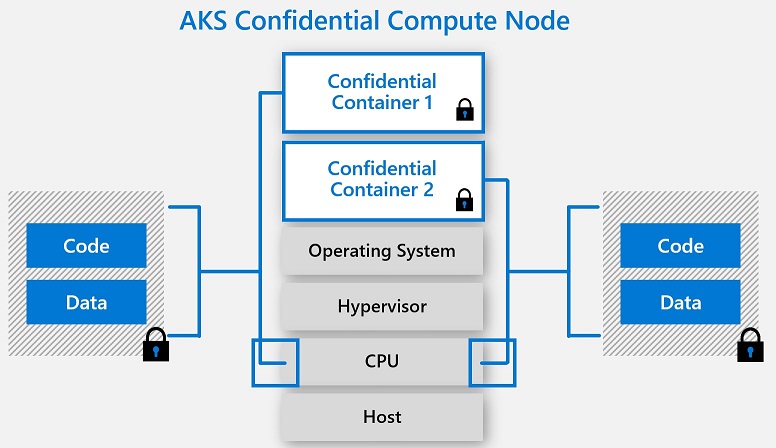
- Hardware based and process level container isolation through SGX trusted execution environment (TEE)
- Heterogenous node pool clusters (mix confidential and non-confidential node pools)
- Encrypted Page Cache (EPC) memory-based pod scheduling
- SGX DCAP driver pre-installed
- Intel FSGS Patch pre-installed
- Supports CPU consumption based horizontal pod autoscaling and cluster autoscaling
- Out of proc attestation helper through AKS daemonset
- Linux Containers support through Ubuntu 18.04 Gen 2 VM worker nodes.
AKS Confidential Nodes deployment:
# - Requirements
az extension add --name aks-preview
az extension list
az extension update --name aks-preview
az feature register --name Gen2VMPreview --namespace Microsoft.ContainerService
az feature list -o table --query "[?contains(name, 'Microsoft.ContainerService/Gen2VMPreview')].{Name:name,State:properties.state}"
az provider register --namespace Microsoft.ContainerService
#- Creation an AKS cluster
az group create --name myResourceGroup --location westus2
az aks create \
--resource-group myResourceGroup \
--name myAKSCluster \
--node-vm-size Standard_DC2s_v2 \
--node-count 3 \
--enable-addon confcom \
--network-plugin azure \
--vm-set-type VirtualMachineScaleSets \
--aks-custom-headers usegen2vm=true
#- The above command should provision a new AKS cluster with DCs-v2 node pools and automatically install two daemon sets - (SGX Device Plugin & SGX Quote Helper)
az aks get-credentials --resource-group myResourceGroup --name myAKSCluster
Now, we have an AKS Confidential cluster ready, let deploy our first application.
kubectl apply -f hello-world-enclave.yaml kubectl get jobs -l app=sgx-test kubectl logs -l app=sgx-test
Maxime.


