Hi!
In this article, I will show you how you add a custom policy to Azure Security Center Recommendation.
These recommendations are based on industry best practices, which are incorporated into the generic, default security policy supplied to all customers. They can also come from Security Center’s knowledge of industry and regulatory standards.
With this feature, you can add your own custom initiatives. You’ll then receive recommendations if your environment doesn’t follow the policies you create.
In the Azure Security Center Portal, please select “Regulatory compliance” under “Cloud Security”.
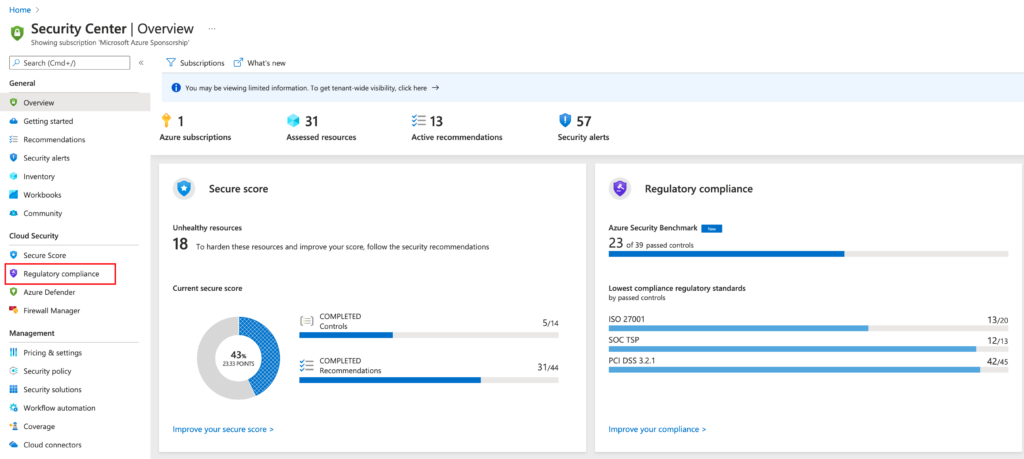
Select, “Manage compliance policies”
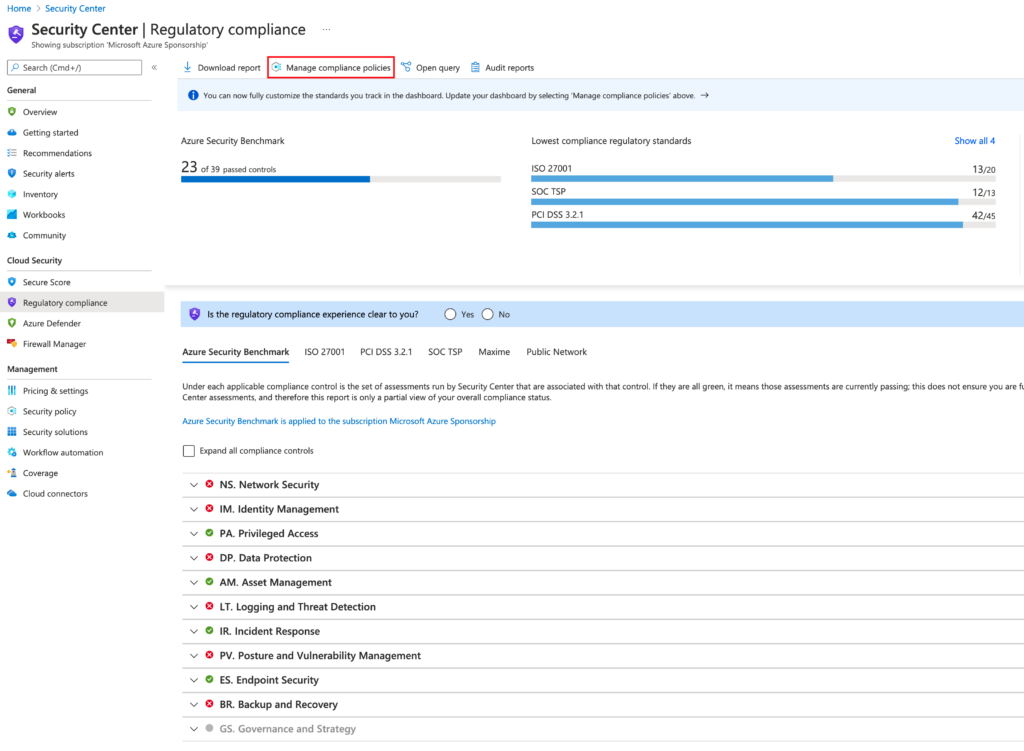
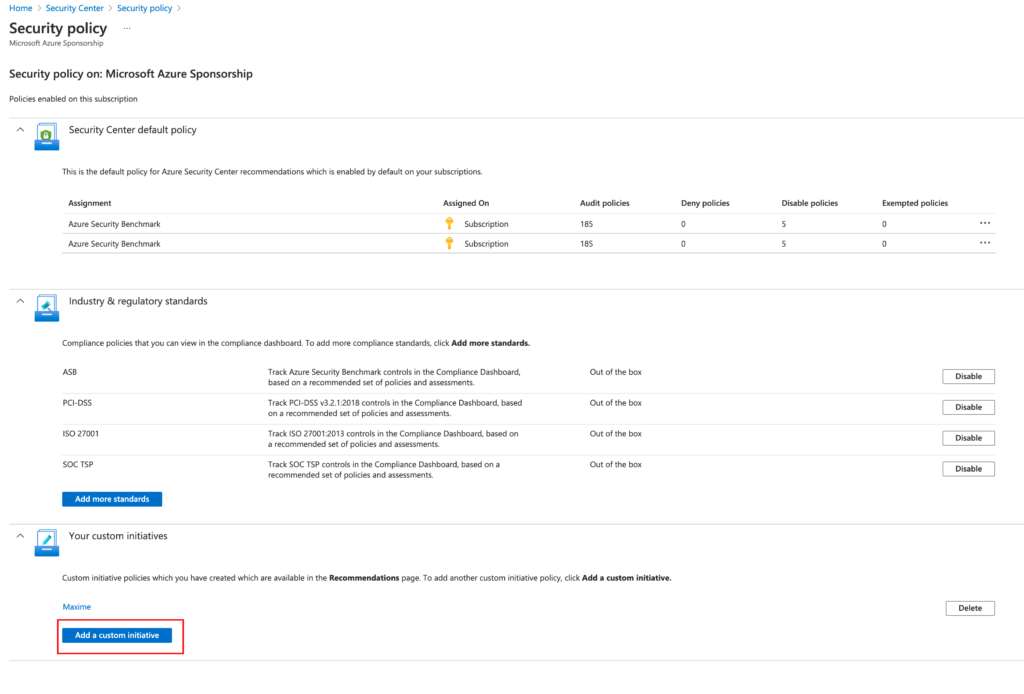
Select “Add a custom initiative”
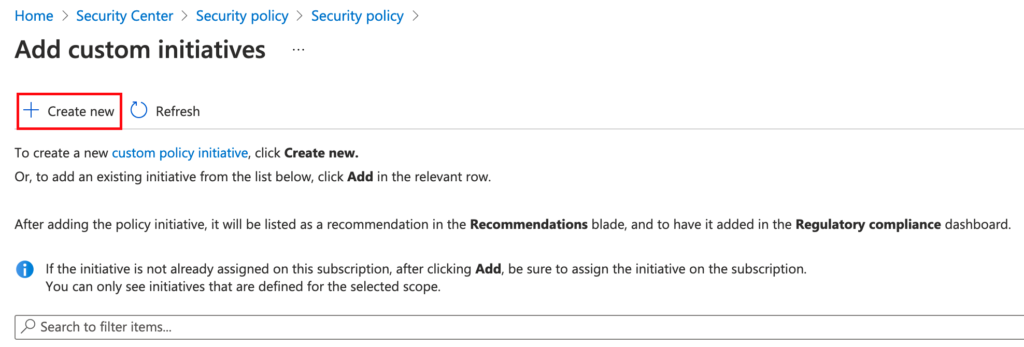
Select, “Creare New”
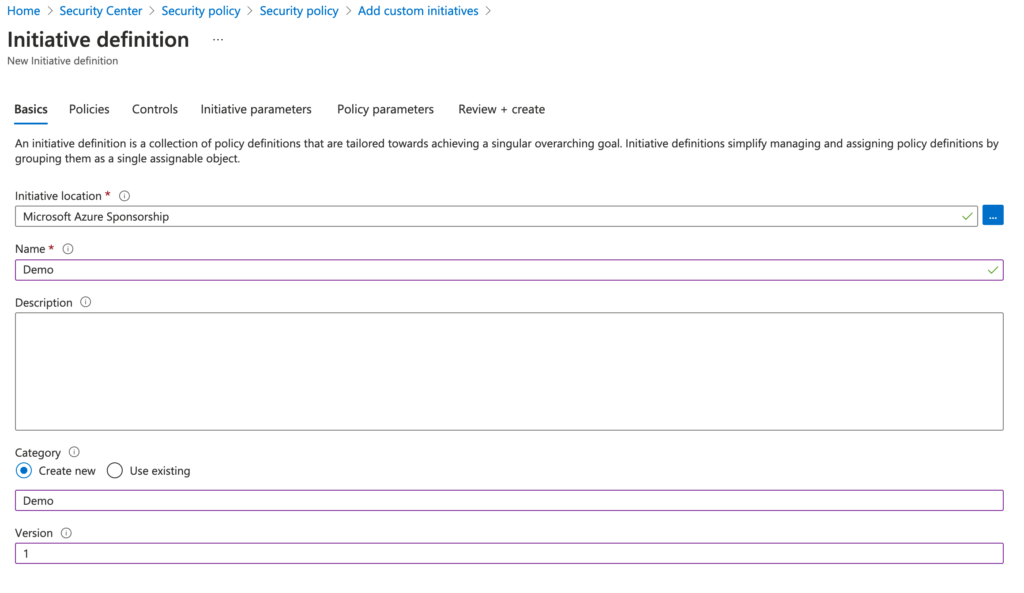
Please define:
- Initiative location
- Demo (Name of your custom initiative, for example XYZ Security Controls)
- Category > Create new > Demo (Your category name could be storage, network, …)
- Version 1
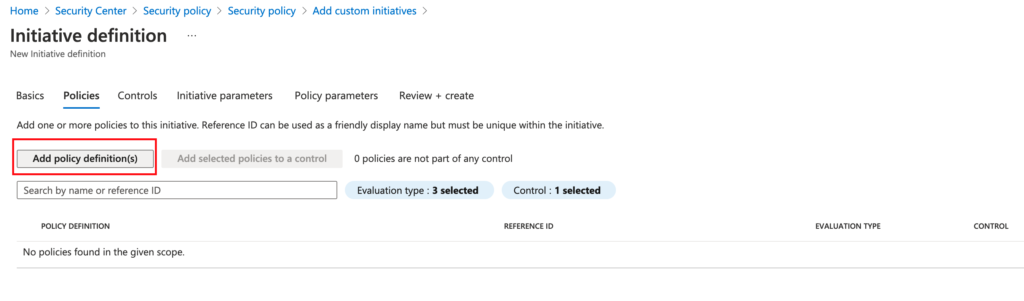
Select “Add policy definition(s)”
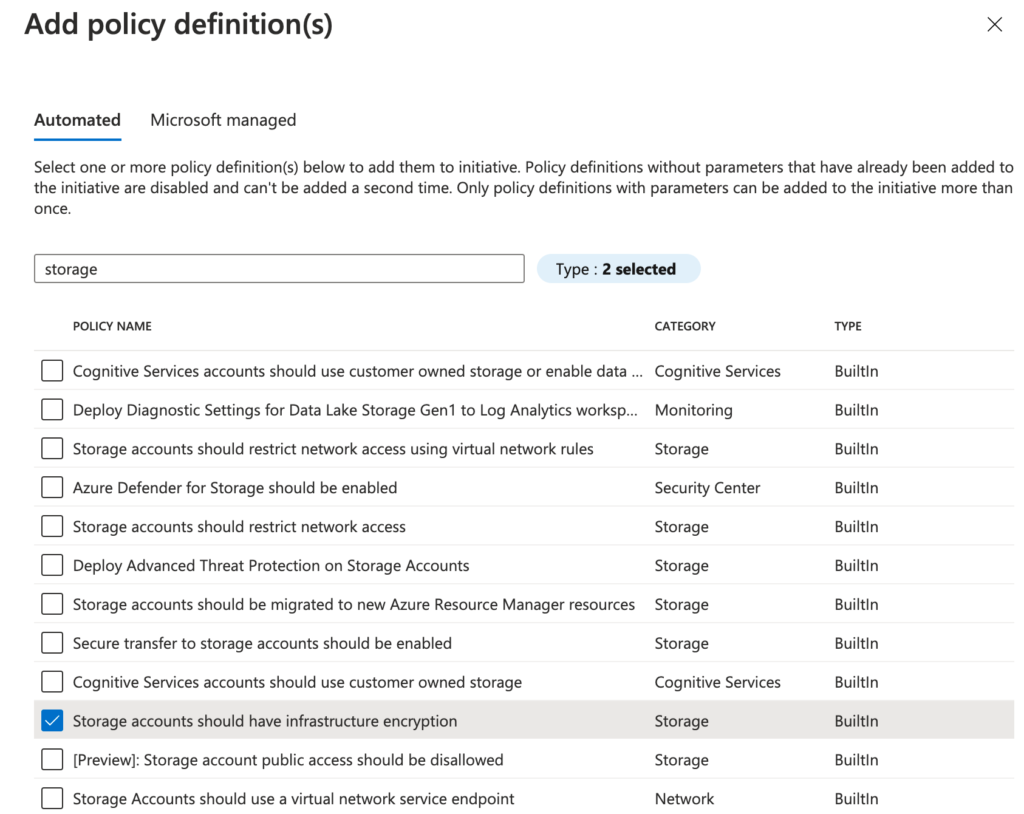
Select your policies, in this example: “Storage accounts should have infrastructure encryption”
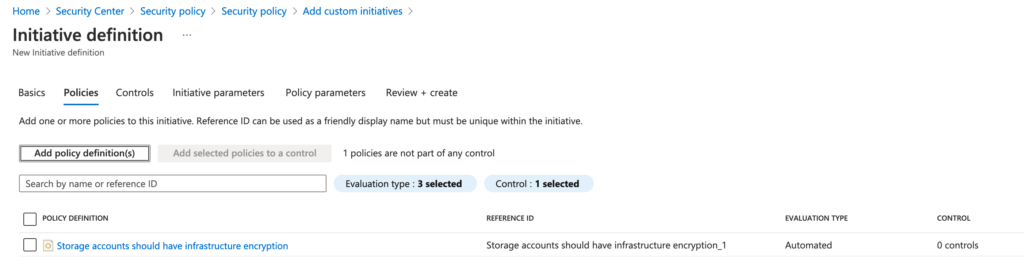
Select “Create Control”
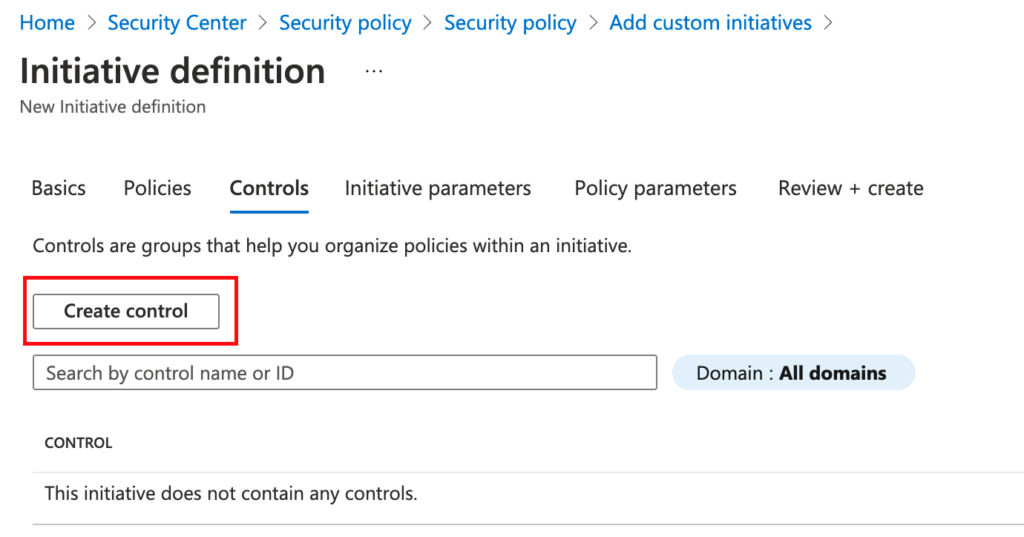
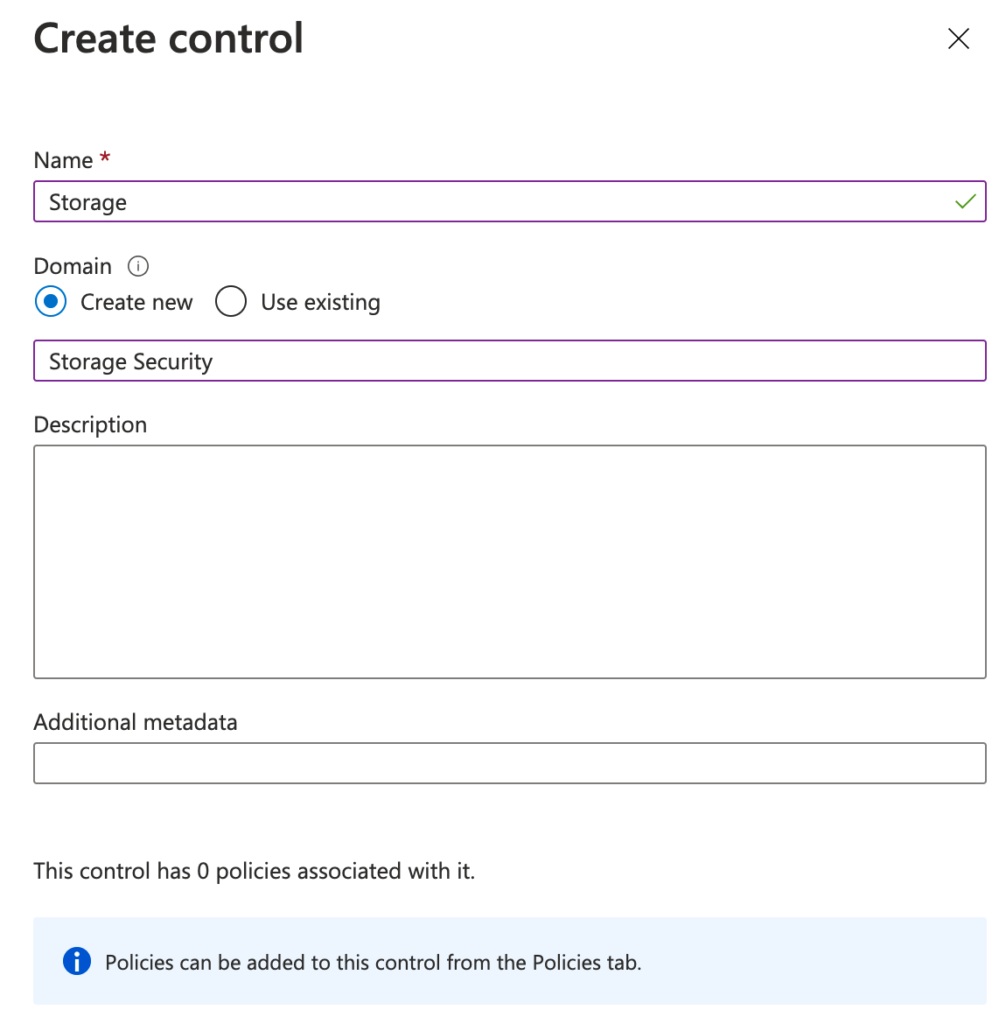
Define a new control, in this example Storage, with the Domain Storage security

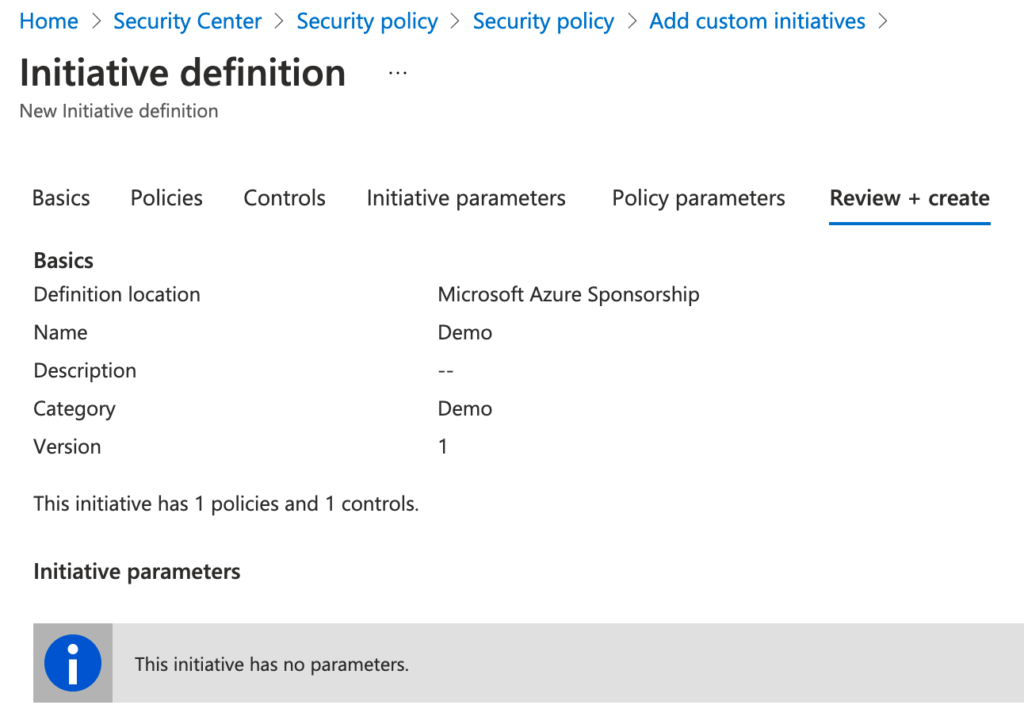
Now the custom initiatives is created, please click on “add”.
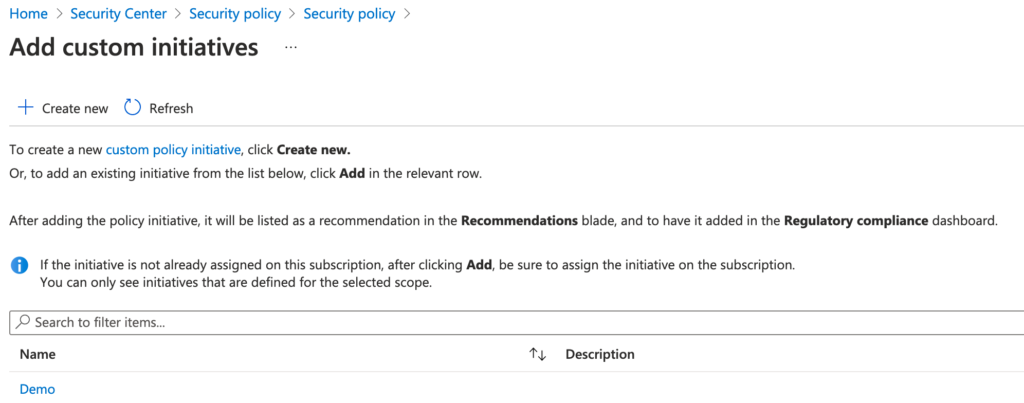
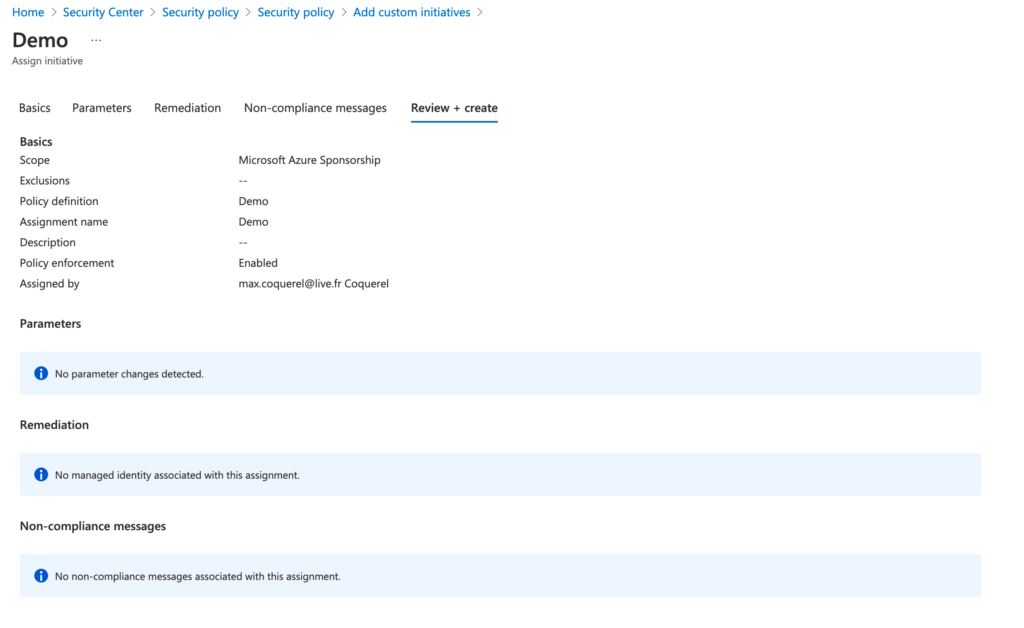
Please find wait 1 hours before to see our custom initiative in the Azure Security Center Recommendation section.
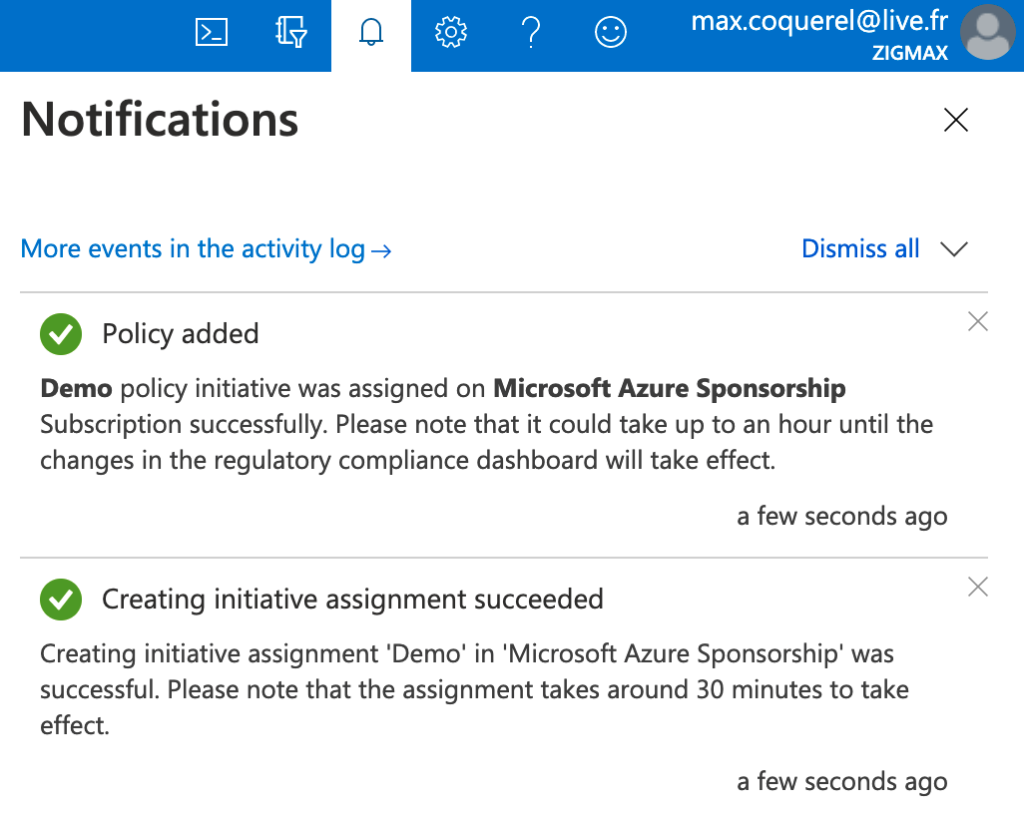
After 1 hours, we can see our custom initiative in the Azure Security Center Recommendation section:
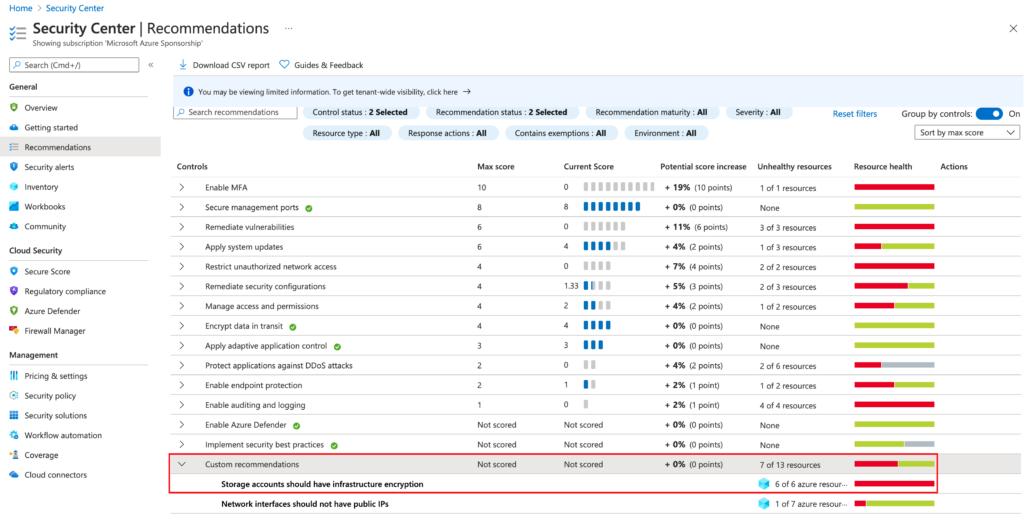
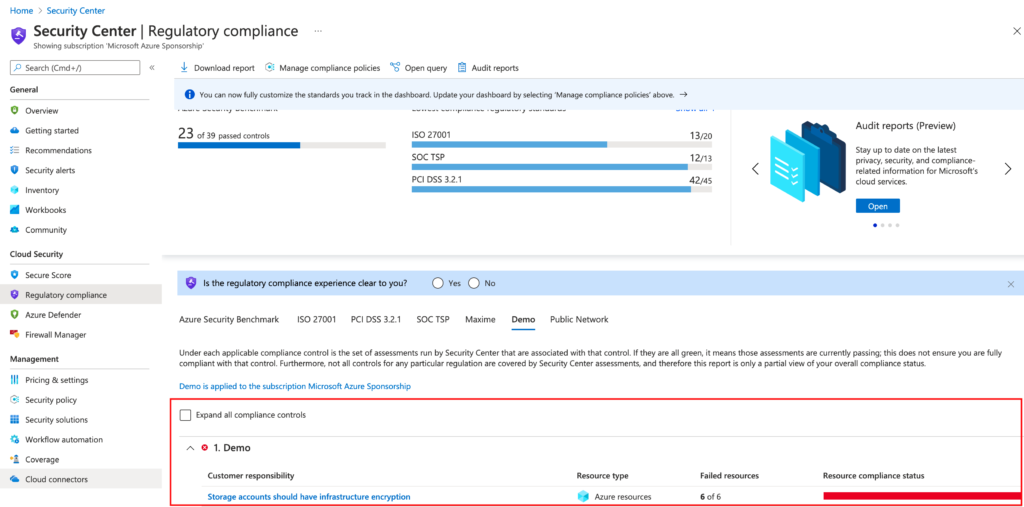
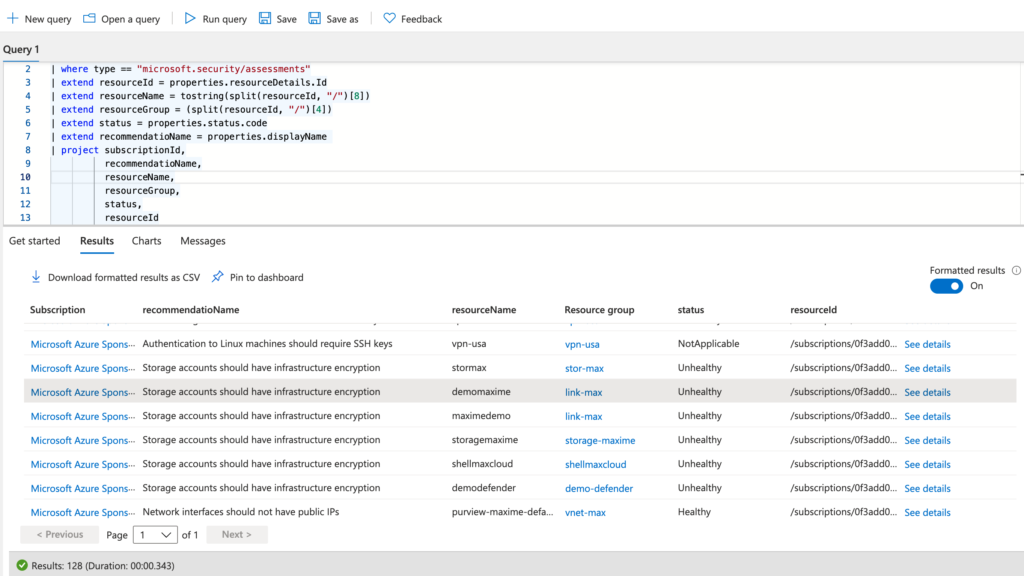
It’s also possible to Azure Resource Graph to see this custom policies.
securityresources | where type == "microsoft.security/assessments" | extend resourceId = properties.resourceDetails.Id | extend resourceName = tostring(split(resourceId, "/")[8]) | extend resourceGroup = (split(resourceId, "/")[4]) | extend status = properties.status.code | extend recommendatioName = properties.displayName | project subscriptionId, recommendatioName, resourceName, resourceGroup, status, resourceId
Maxime.


