Hi!
In this article, I will show you how you can scan an Azure Blob to identity potential public storage containers. By default when you create a new container, you have 3 options to define the public level access:
- Private: No public access to this container (default configuration).
- Blob: Public access is permitted to this container and its blobs.
- Container: Public access is permitted to blobs in this container, but not to the container itself.

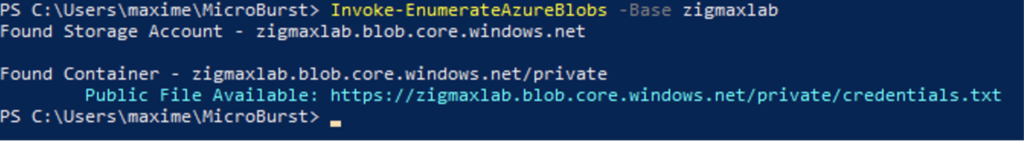
To leverage this attack, we will use a function including in the MicroBurst tool.
Invoke-EnumerateAzureBlobs -Base yourcompanyname
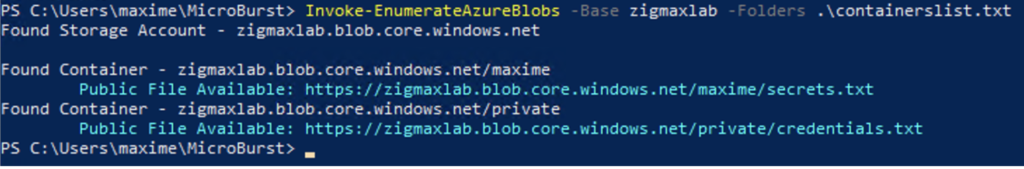
In this example, I will use an additional containerlist file with some folders examples (dev, non, prod, devprod, ….)
Invoke-EnumerateAzureBlobs -Base zigmaxlab -Folders .\containerlist.txt
Maxime.