Hi!
By default, a storage account allows public access to be configured for containers in the account, but does not enable public access to your data. Public access to blob data is never permitted unless you take the additional step to explicitly configure the public access setting for a container.
Microsoft introduced a new protection feature to help avoid public access on storage account. The feature introduces a new property named allowBlobPublicAccess.
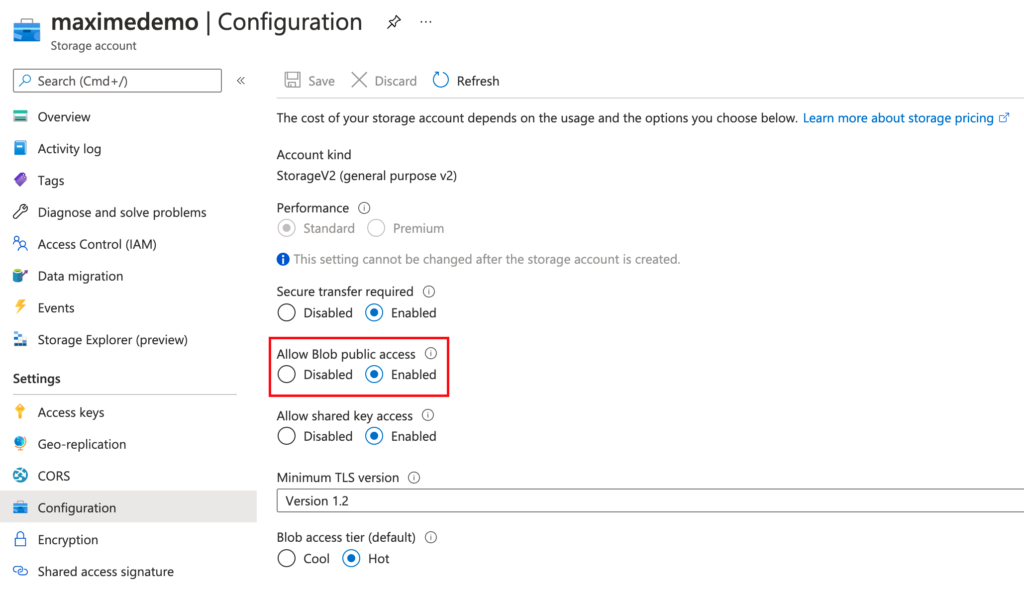
Microsoft recommends that you disallow public access to a storage account unless your scenario requires it. Disallowing public access helps to prevent data breaches caused by undesired anonymous access.
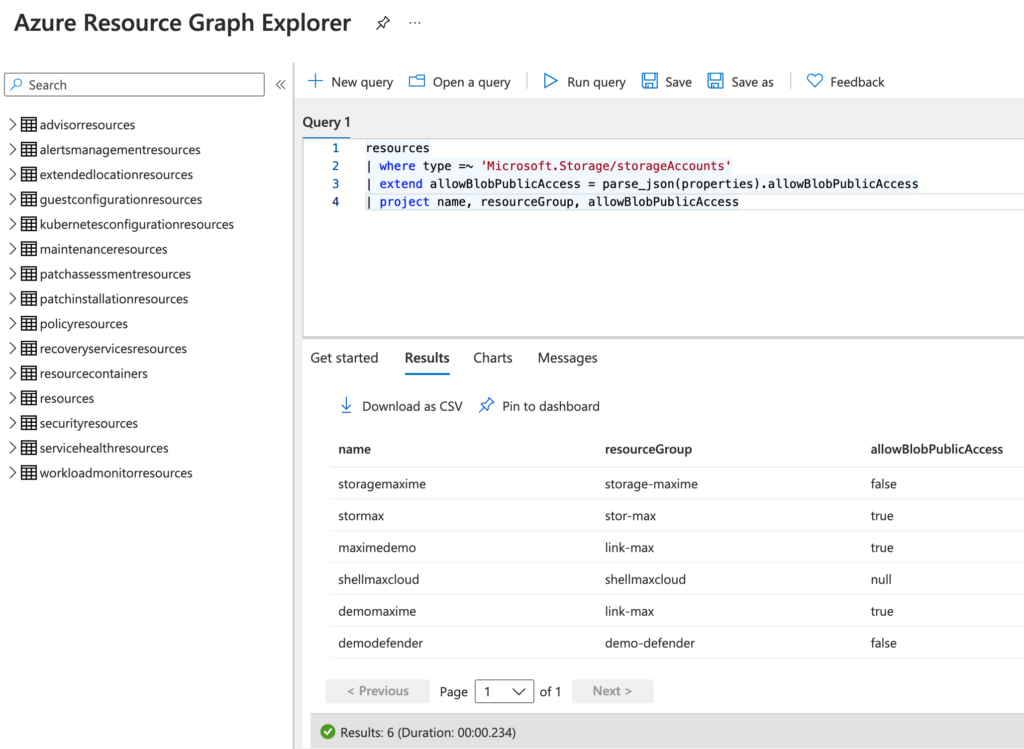
In this article, I will you show you how you can identify these storage accounts with an Azure Graph query:
resources | where type =~ 'Microsoft.Storage/storageAccounts' | extend allowBlobPublicAccess = parse_json(properties).allowBlobPublicAccess | project name, resourceGroup, allowBlobPublicAccess
Few months ago, I written an article to show you how you can identify these storage accounts with an audit Azure Policy: https://zigmax.net/identifier-les-comptes-de-stockage-publiques/ (This article is written in French).
Maxime.


