Hi!
Attackers want to target service principals because:
- Service accounts and service principals do not have MFA
- Attackers can log into Azure using a service principal account
- These accounts exist with all applications in Azure (most companies have several)
- These accounts could be controlled through conditional access only with an Azure Active Directory P2.
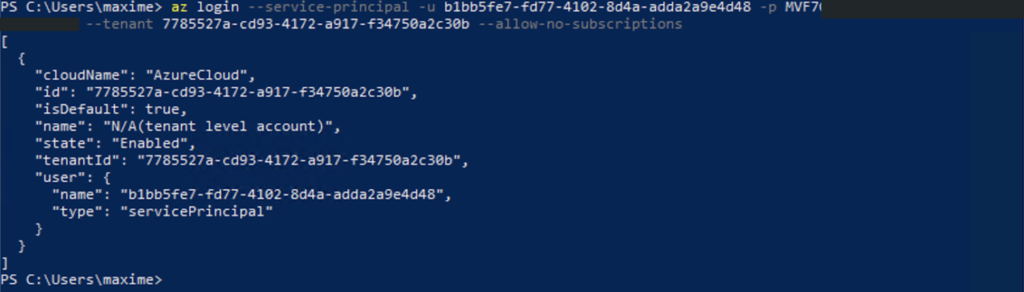
Sign-in with the service principal using Azure CLI:
az login –service-principal -u YourServicePrincipald -p YourServicePrincipalPassword -tenant YourTenantId –allow-no-subscriptions
To prevent this attack, you can define a Conditional Access policies for your service principals. You need to have an Azure Active Directory Premium P2 to enable this feature.
- https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/workload-identity
- https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-location
Maxime.


